12 risk-based authentication tools compared
CSO Magazine
MARCH 1, 2022
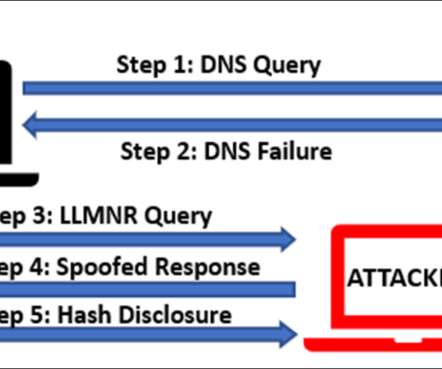
Risk-based authentication (RBA), also called adaptive authentication, has come of age, and it couldn’t happen fast enough for many corporate security managers. What is risk-based authentication? It creates a risk profile of the person or device requesting access to the system.















































Let's personalize your content