Should You Backup Office 365? And If Yes, Then How?
Spinone
JANUARY 24, 2021
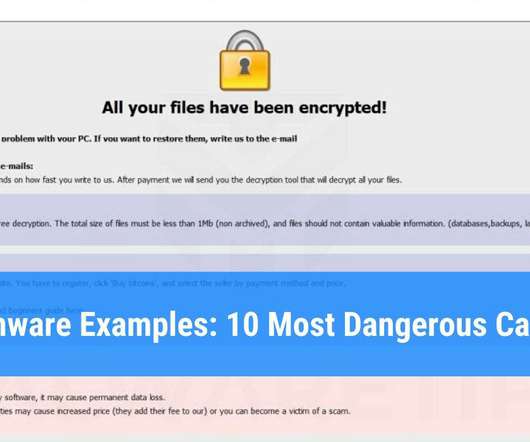
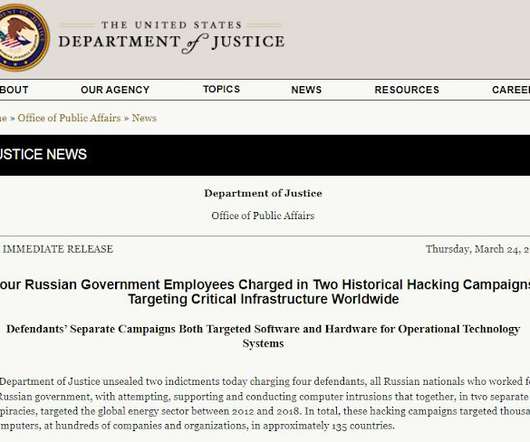
This article was updated in January 2021. So, should you backup your Office 365 data? Such risks are one of the key concerns expressed by our customers when considering our backup. If something happens from Microsoft’s side, you won’t be able to reach your data and continue working unless you have a backup.
















































Let's personalize your content