Artificial Intelligence blocks RYUK Ransomware invasion
CyberSecurity Insiders
APRIL 12, 2022
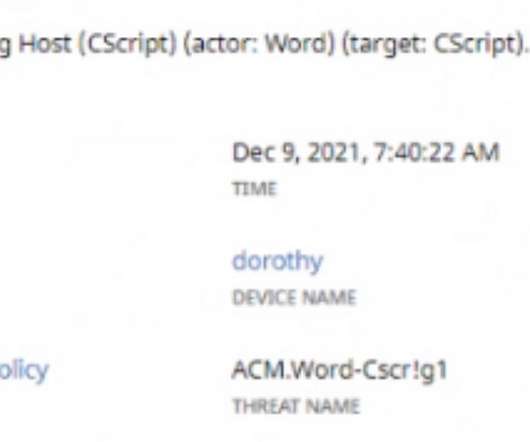
Interestingly, this gang of cyber crooks is also known to target backup systems meant to recover information and resources at the time of the disaster. And it does so by employing Artificial Intelligence technology into its threat monitoring and mitigation services. .


















































Let's personalize your content