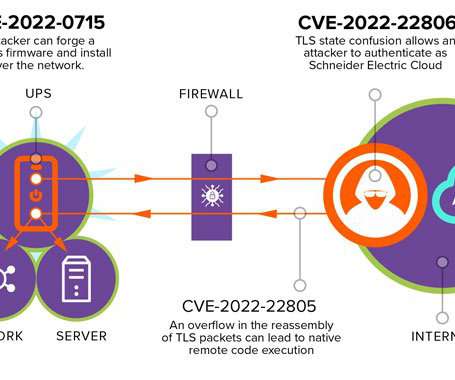
TLStorm flaws allow to remotely manipulate the power of millions of enterprise UPS devices
Security Affairs
MARCH 9, 2022
Uninterruptible power supply (UPS) devices provide emergency backup power for mission-critical systems. Two of the TLStorm vulnerabilities reside in the TLS implementation used by Cloud-connected Smart-UPS devices, while the third one is a design flaw in the firmware upgrade process of Smart-UPS devices. ” continues Armis.






































Let's personalize your content