New TunnelVision technique can bypass the VPN encapsulation
Security Affairs
MAY 8, 2024
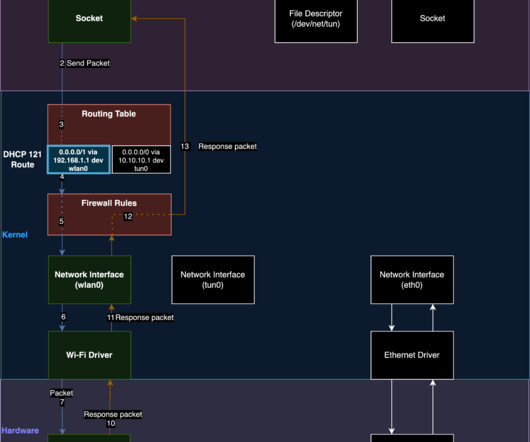
TunnelVision is a new VPN bypass technique that enables threat actors to spy on users’ traffic bypassing the VPN encapsulation. Leviathan Security researchers recently identified a novel attack technique, dubbed TunnelVision, to bypass VPN encapsulation. The researchers referred to this result as “decloaking.”
















































Let's personalize your content