The Importance of Family Identity Theft Protection
Identity IQ
SEPTEMBER 15, 2023
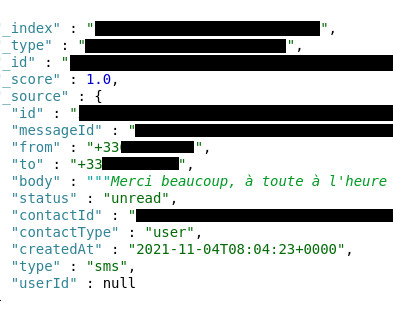
The Importance of Family Identity Theft Protection IdentityIQ In today’s interconnected world, your family’s digital footprint grows every time you click, post, or shop online. million American children were victims of identity fraud last year? million American children were victims of identity fraud last year?












































Let's personalize your content