Dropbox Sign Data Breach: What You Need to Know and How to Protect Yourself
Penetration Testing
MAY 1, 2024
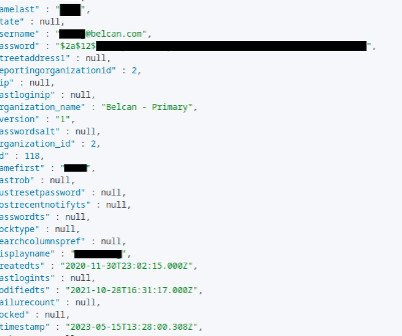
Dropbox confirmed a security breach on April 24th within its Dropbox Sign (formerly HelloSign) service, exposing customer data including email addresses, usernames, phone numbers, and hashed passwords.














































Let's personalize your content