Akira Ransomware Targeting VPNs without Multi-Factor Authentication
Cisco Security
AUGUST 24, 2023
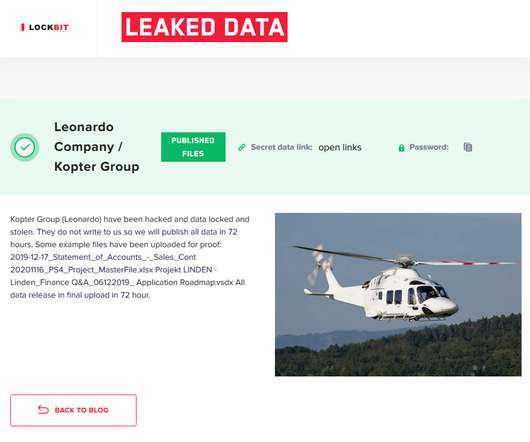
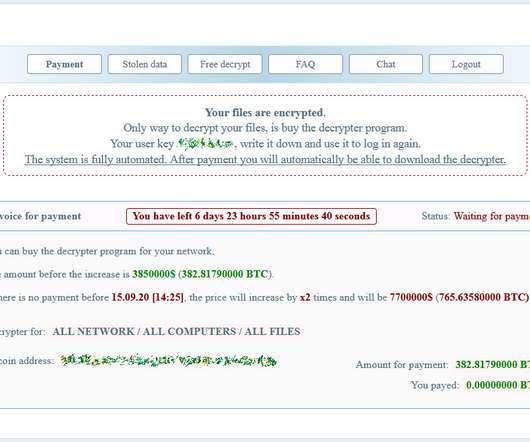
Cisco is aware of reports that Akira ransomware threat actors have been targeting Cisco VPNs that are not configured for multi-factor authentication to infiltrate organizations, and we have observed instances where threat actors appear to be targeting organizations that do not configure multi-factor authentication for their VPN users.

















































Let's personalize your content