Enhance your security posture by detecting risks on authenticator devices
Thales Cloud Protection & Licensing
MARCH 17, 2022
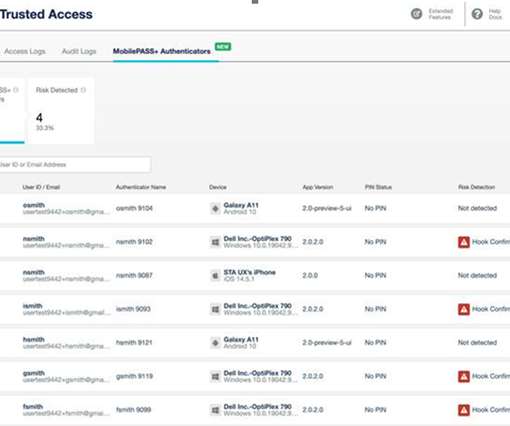
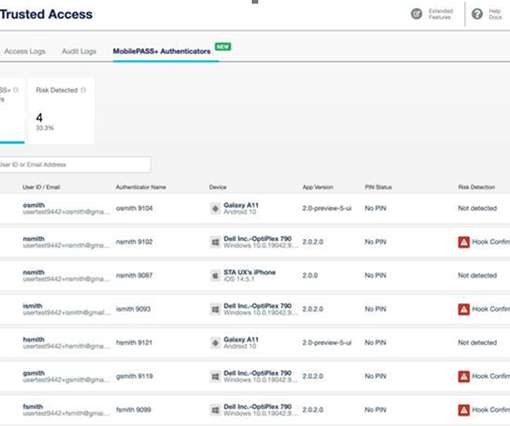
Enhance your security posture by detecting risks on authenticator devices. Not only are mobile devices used as end points to access corporate mail and other enterprise applications, they are also frequently used as authentication devices. Limited visibility on users’ devices can undermine authentication integrity.















































Let's personalize your content