Windows Hello fingerprint authentication can be bypassed on popular laptops
Malwarebytes
NOVEMBER 24, 2023
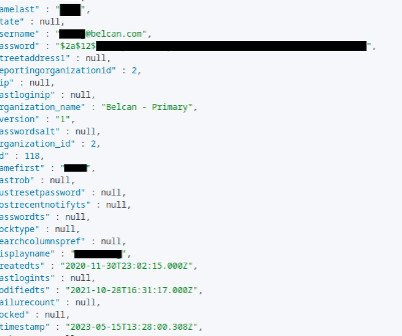
Researchers have found several weaknesses in Windows Hello fingerprint authentication on Dell Inspiron 15, Lenovo ThinkPad T14, and Microsoft Surface Pro X laptops. They found vulnerabilities that allowed them to completely bypass Windows Hello authentication on all three. The input has to be authenticated.














































Let's personalize your content