Hacked IoT Devices Livestreaming Swatting Attacks: FBI
Adam Levin
DECEMBER 30, 2020
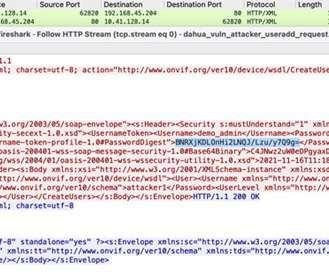
Hackers are using internet-connected home devices to livestream “swatting” attacks, according to the FBI. In the latest wave of attacks, hackers are using credential stuffing, where credentials from previously compromised accounts are used to gain access to internet-enabled smart home devices. “As











































Let's personalize your content