Phorpiex botnet sent millions of phishing emails to deliver LockBit Black ransomware
Security Affairs
MAY 13, 2024
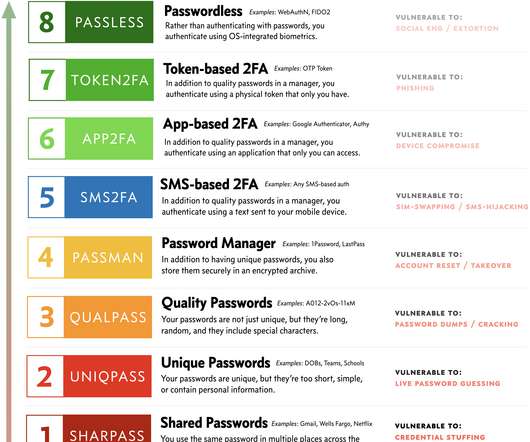
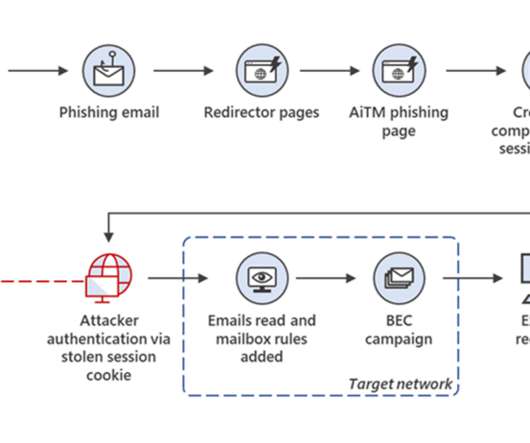
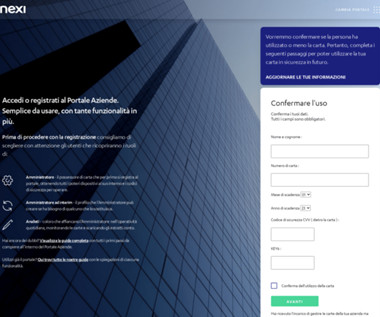
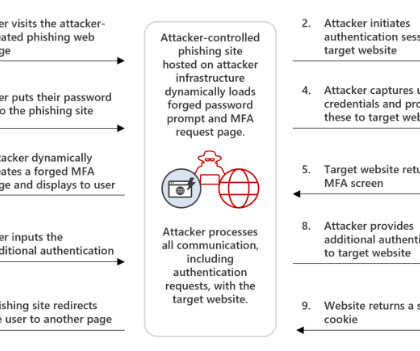
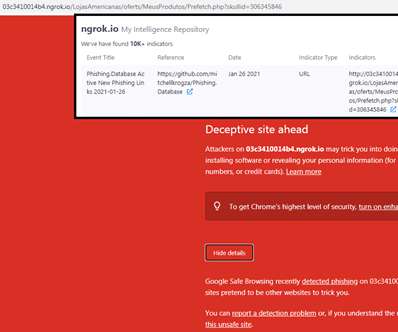
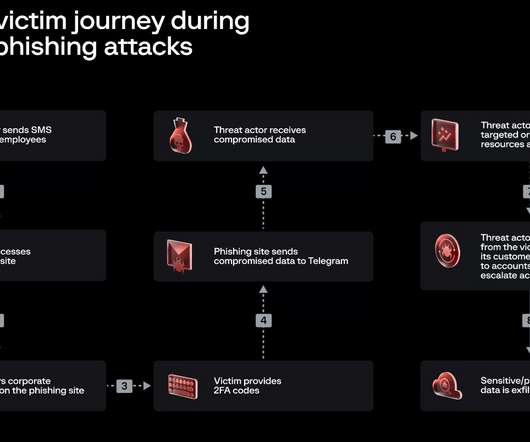
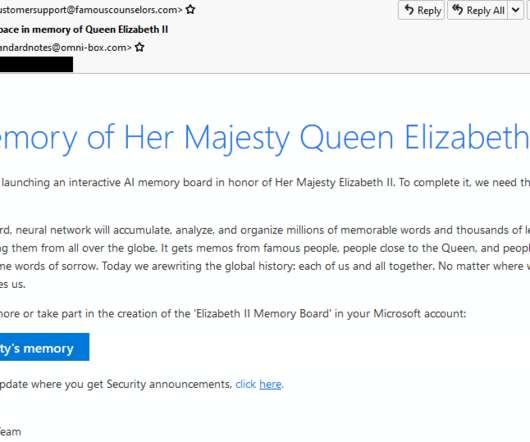
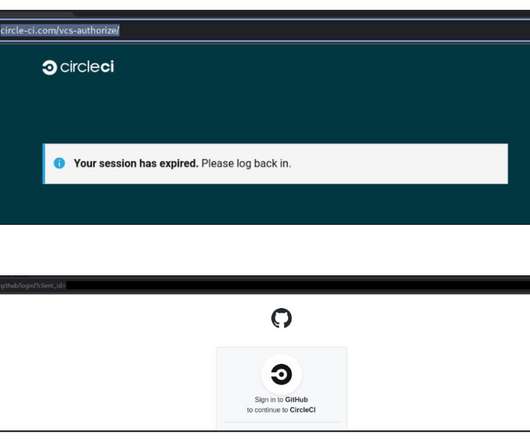
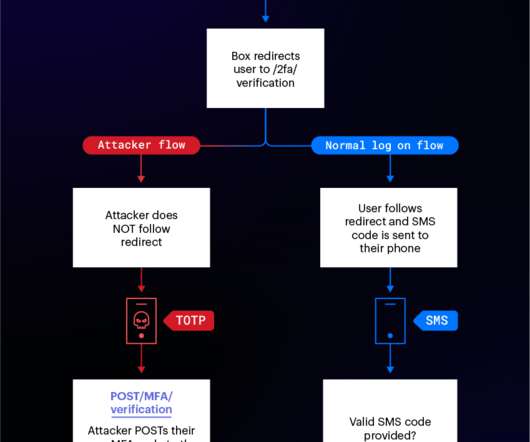
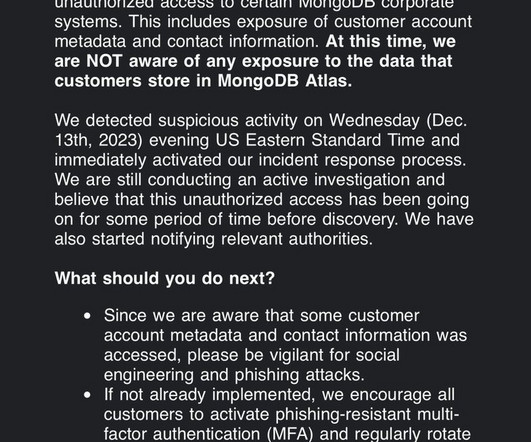
Experts reported that since April, the Phorpiex botnet sent millions of phishing emails to spread LockBit Black ransomware. Password Management : Use strong, unique passwords and implement multi-factor authentication (MFA) whenever possible, prioritizing authentication apps or hardware tokens over SMS text-based codes.






























Let's personalize your content