Axiad and Okta Partner to Revolutionize Authentication with Phishing Resistant MFA
Security Boulevard
SEPTEMBER 25, 2023
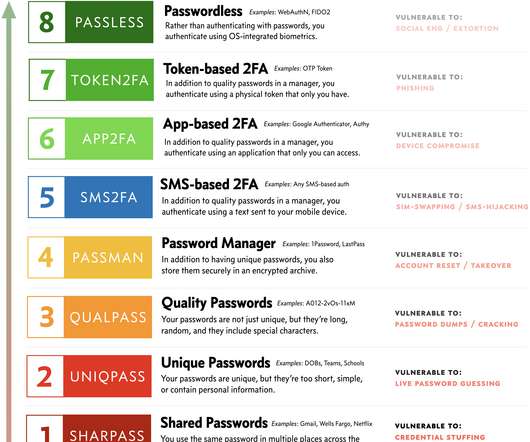
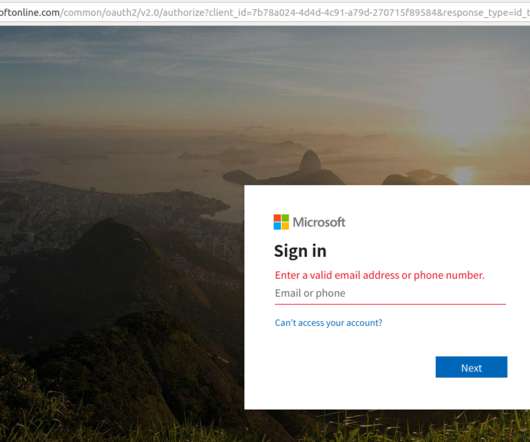
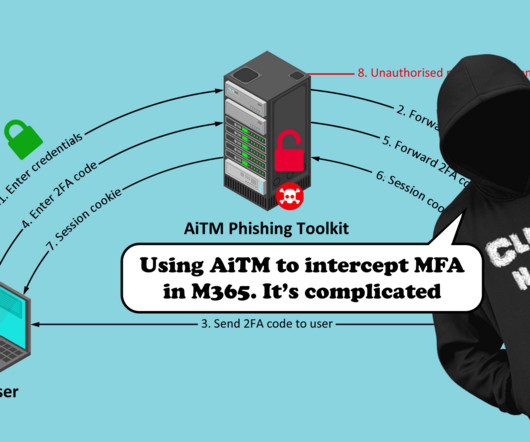
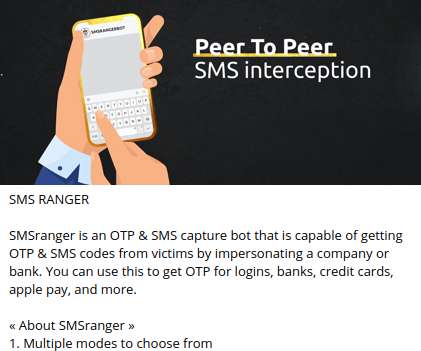
Passwords present several pain points, both from a security and usability standpoint. The post Axiad and Okta Partner to Revolutionize Authentication with Phishing Resistant MFA appeared first on Axiad. Malicious actors can.












































Let's personalize your content