US cyber and law enforcement agencies warn of Phobos ransomware attacks
Security Affairs
MARCH 2, 2024
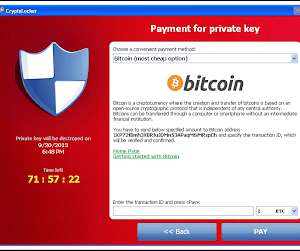
Threat actors behind Phobos attacks were observed gaining initial access to vulnerable networks by leveraging phishing campaigns. After SmokeLoader’s hidden payload is downloaded onto the victim’s system, threat actors use the malware’s functionality to download the Phobos payload and exfiltrate data from the compromised system.











































Let's personalize your content