New RomCom RAT Campaign Abusing Well-Known Software Brands
Heimadal Security
NOVEMBER 4, 2022
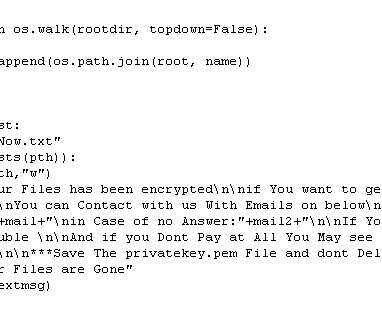
Malware is disguised as a legitimate program on fake websites that imitate official download portals for SolarWinds Network Performance Monitor (NPM), KeePass password manager, PDF Reader Pro, and Veeam Backup and […].
































Let's personalize your content