QNAP fixed second zero-day demonstrated at Pwn2Own Ireland 2024
Security Affairs
OCTOBER 31, 2024
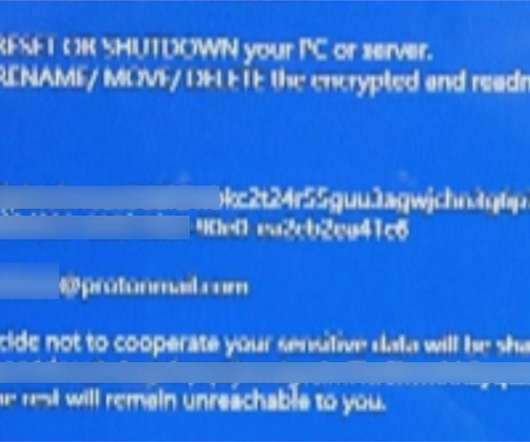
QNAP addressed the second zero-day vulnerability demonstrated by security researchers during the recent Pwn2Own Ireland 2024. Taiwanese manufacturer QNAP patched the second zero-day vulnerability, tracked as CVE-2024-50387 , which was exploited by security researchers during the recent Pwn2Own Ireland 2024.







































Let's personalize your content