Security Awareness Training across an SMB Organization
Spinone
MARCH 20, 2019
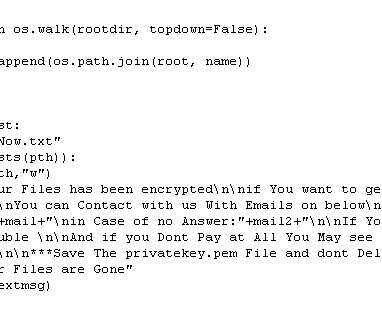
When considering a fully-featured and well thought out security plan , the human factor is an extremely important part of the equation, and arguably just as important as the technology component of the solution. In this article, we will take a look at cyber security awareness across an SMB organization.


















































Let's personalize your content