Data Privacy Week 2022: The Security Awareness Canary in the Coalmine
Webroot
JANUARY 24, 2022
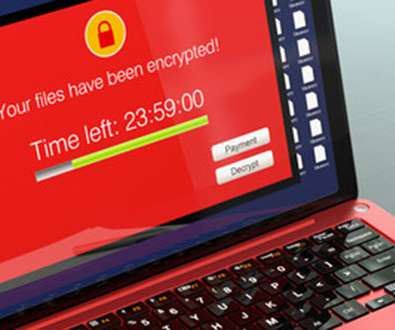
Whether it’s for your home or your business, ensure you take privacy into account when you agree to the terms and conditions of items available for download from the internet or when you create a program that may expose your employees to online risk. Some providers offer free protection and backup solutions, but can you really trust them?


















































Let's personalize your content