Nearly 10 Billion Passwords Leaked in Biggest Compilation of All Time
Tech Republic Security
JULY 9, 2024
Nearly 10 billion passwords have been leaked on a popular hacking forum, according to Cybernews.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JULY 9, 2024
Nearly 10 billion passwords have been leaked on a popular hacking forum, according to Cybernews.

Tech Republic Security
MAY 9, 2023
Changing an Apple ID password typically isn't as simple as just entering a replacement password. The post Apple ID: 3 things to remember when changing this password appeared first on TechRepublic. Prepare more effectively for the process by remembering three key facts.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
OCTOBER 16, 2019
Related: Cyber risks spinning out of IoT Credential stuffing and account takeovers – which take full advantage of Big Data, high-velocity software, and automation – inundated the internet in massive surges in 2018 and the first half of 2019, according to multiple reports. Rapid 7 estimates that there are upwards of 1.5

Security Affairs
APRIL 15, 2025
A critical flaw (CVE-2025-24859, CVSS 10) in Apache Roller lets attackers keep access even after password changes. where active user sessions are not properly invalidated after password changes. where active user sessions are not properly invalidated after password changes. This impacts big-data frameworks (e.g.,

Tech Republic Security
JULY 26, 2017
Lastwall co-founder and CEO Karl Holmqvist explains how artificial intelligence could could soon eliminate the need for password-based security.

Krebs on Security
SEPTEMBER 17, 2020
But in the days that followed, several antivirus products began flagging it for bundling at least two trojan horse programs designed to steal passwords from various online gaming platforms. “SonarX served as an easily searchable repository for social media data that previously had been obtained by CHENGDU 404.” Image: DOJ.

Thales Cloud Protection & Licensing
JUNE 12, 2018
In this age of big data, the concept is fitting, because this kind of information is increasingly being used to identify individuals and even machines. For years identity management has relied on three factors for authentication: What one knows (passwords). Big Data Analytics. What one has (tokens).

Security Affairs
AUGUST 29, 2019
Last week, Cisco released security fixes to address 17 critical and high-severity vulnerabilities affecting some Cisco Unified Computing products, including Integrated Management Controller (IMC), UCS Director, and UCS Director Express for Big Data. ” wrote the expert. ” reads the security advisory published by Cisco.

Malwarebytes
MAY 10, 2024
Email addresses are a unique identifier that can allow data brokers to merge and enrich their databases. So, this is another big data breach that leaves us with more questions than answers. We have to be careful that we don’t shrug these data breaches away with comments like “they already know everything there is to know.”

CyberSecurity Insiders
JANUARY 4, 2023
Adding more embarrassment to last year’s Twitter Data Breach, a new finding on the web has discovered a new database dump exposed on an online hacking forum. It appears to be a big data leak as information related to about 235 million users was found by a cyber intelligence firm named Hudson Rock, based in Israel.

Security Affairs
JUNE 29, 2019
Attunity data integration and big data management firm exposed a significant amount of sensitive data through unprotected Amazon S3 buckets. Data integration and big data management firm Attunity exposed a significant amount of sensitive data through unprotected Amazon S3 buckets.

The Last Watchdog
JUNE 19, 2024
Perhaps the biggest change lies in the way the rules are generated and maintained, where once a pool of highly skilled and experienced cybersecurity analysts iterated and codified actions as lovingly-maintained rules, today big data systems power machine learning systems to train complex classifiers and models.

CyberSecurity Insiders
APRIL 16, 2021
Scenarios such as information leaks, wiretapping, and data breaches can compromise your organization. Considering that we are in the age of big data, it has become easier for anyone — including cybercriminals — to acquire sensitive information. . Use a secure conferencing app.

eSecurity Planet
AUGUST 4, 2022
Attackers can intercept data transfers, and from there gain access to all manner of sensitive data. Thus, data in transit, as well as data at rest, should be made indecipherable via strong encryption. By encrypting data, it can only be accessed with the right password and by those with the appropriate access rights.

The Last Watchdog
JULY 11, 2018
We secure the people by giving them usernames and passwords, which they use to get on the network of machines. LW: This implies big data sets, which is perfect for machine learning. LW: Can you frame what’s going on with identities when it comes to digital transformation? Hudson: Sure. Hudson: Yes, exactly.

Thales Cloud Protection & Licensing
APRIL 23, 2018
94 percent of respondents are using sensitive data in cloud, big data, IoT or mobile environments. But with widespread enterprise adoption of cloud technologies, come very real data security risks. 42 percent are using 50 or more Software as a Service (Saas) applications.

IT Security Guru
AUGUST 31, 2022
Technical factors that can lead to broken authentication in APIs include, among others, weak password complexity, missing account lockout thresholds, excessively long durations for password/certificate rotations, or use of API keys as the only authentication material.

Security Affairs
MAY 19, 2023
” The Guerrilla malware has a modular structure, each plugin was designed to support a specific feature, including: SMS Plugin : Intercepts one-time passwords sent via SMS. The Lemon Group’s method is similar to Xposed framework development , with both modified zygote processes to implement global process injection.”

Tech Republic Security
JULY 18, 2023
Use this comprehensive list of strategies to help you safeguard your company's data from threats and data breaches.

Tech Republic Security
AUGUST 14, 2023
Discover strategies for securing data on your personal Mac for work tasks. Learn how to protect your device against potential threats.

eSecurity Planet
AUGUST 22, 2023
Your company stakeholders — especially the employees — should know the strategies your security team is using to prevent data breaches, and they should know simple ways they can help, like password protection and not clicking on malicious links or files or falling for phishing attacks.

eSecurity Planet
MARCH 9, 2023
Guardium Vulnerability Assessment tool scans the databases, data warehouses, data lakes , and other components of big data infrastructure to detect vulnerabilities based on Security Technical Implementation Guides (STIG), Center for Internet Security (CIS), CVE , and other standards.

Thales Cloud Protection & Licensing
JUNE 14, 2018
In this blog, and in an accompanying one by my Thales colleague Juan Asenjo, we will discuss the subject of big data analytics, and how it is enabling a new behavior-based authentication evolution for easier and more robust identity management.
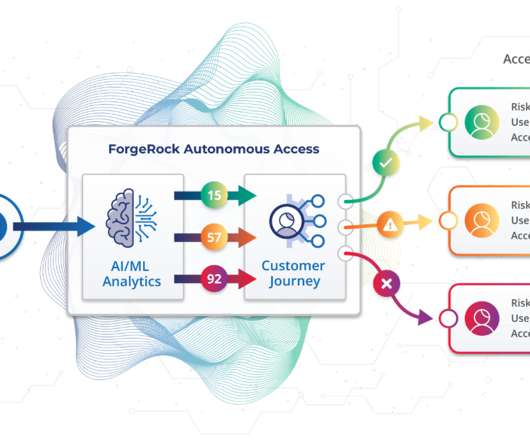
Security Boulevard
JUNE 7, 2022
Breaches containing usernames and passwords increased 450% in 2020, totaling 1.48 According to a recent Javelin Research report Identity Fraud Study: The Virtual Battleground , account takeover increased by 90% to an estimated $11.4 billion in 2021 when compared with 2020. billion breached records.

eSecurity Planet
JUNE 17, 2021
With the EDB PostgreSQL Advanced Server, clients gain features like password profiles, enhanced audit logging, and data redaction. Features include automated discovery, port scans and patch status, password integrity , and protections for database-specific risks. Read our in-depth review of the McAfee Data Center Security Suite.

Security Boulevard
JUNE 15, 2021
Protecting your passwords, financial, and other private data safe and secured from hackers is very important for businesses and one's privacy, it is increasingly vital for consumers and individuals to follow data protection guidance and use good strategies to help secure their sensitive or private information safe and protected.

Malwarebytes
JANUARY 23, 2022
It essentially allows big data-gathering companies to continue doing what they have been doing,” Ruane said. At this point, it’s easy to think that US data privacy rights are following a sad trend of one step forward, two steps back. With a VPN, your traffic is encrypted and illegible to outside parties.

Webroot
MARCH 4, 2024
Fortify Your Digital Armor: Use security software, VPNs, strong passwords, and two-factor authentication. Imagine a world where your news feed aligns perfectly with your interests, introducing you to relevant content. But this is only the tip of the iceberg. Verify information before sharing or acting upon it. Regularly update your software.

Centraleyes
JULY 16, 2024
In the era of big data , companies generate and store vast amounts of information. This data takes many forms, ranging from highly confidential data to less sensitive analytics. Cloud services offer many advantages for data management, including scalability, cost efficiency, and enhanced collaboration.

Spinone
DECEMBER 26, 2018
Today, c yber security incidents lead to significant damage, alarming organizations of all types and sizes in different geographic locations. I’m not exaggerating: A s ecure cloud backup solution can save hours, days, months and years of your team’s work.

ForAllSecure
DECEMBER 21, 2022
Here are some air travel tips from The Art of Invisibility: The World's Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data by Kevin Mitnick and Robert Vamosi. In the United States, you can be compelled to provide your fingerprint, but you cannot be compelled to provide your password.

eSecurity Planet
APRIL 26, 2022
Lightspeed’s enterprise sectors beyond cybersecurity include big data, SaaS, crypto, and IT services. Notable cybersecurity exits for the company include Forescout, Imperva, Webroot, Tenable, and Crowdstrike; and Accel’s other successful investments include Atlassian, Cloudera, Etsy, and Meta. Accel Investments.

Security Boulevard
JUNE 26, 2023
Weak access and permissions, therefore, may cause data breaches through: Inadequate authentication – weak verifications can result in data breaches by unauthorized employees in the organization. Yahoo also recorded a breach that affected 1 billion accounts in 2013, where names and passwords were stolen.

Security Boulevard
JUNE 1, 2021
Use of weak passwords was a common theme with the investigation, which concluded: weak default passwords cyber-criminals could hack were found on most of the routers. computing editor Kate Bevan said that a proposed UK Smart Device legislation which would ban default passwords on routers " can't come soon enough. At least 4.5

Krebs on Security
DECEMBER 14, 2023
Even if one managed to steal (or guess) a user’s DirectConnection password, the login page could not be reached unless the visitor also possessed a special browser certificate that the forum administrator gave only to approved members. A screen shot of the org chart from ChronoPay’s MegaPlan Intranet system.

Security Affairs
MAY 2, 2022
It is easy to forget that our data will probably be warehoused and crunched by an external multi-million dollar data warehousing and analysis company, not the friendly, trustworthy folks at the customer service center. Big Data storage systems have weaknesses. And so, the data breaches keep getting bigger.

ForAllSecure
APRIL 4, 2023
And then you go and help the customer on site because the data is on site and you need to actually kind of get hands on to the point we used to do imaging in big data centers and stuff and it take hours because terabytes of data and you'd have people sleeping in the data center, like which is crazy.

Thales Cloud Protection & Licensing
JUNE 9, 2021
Front Door : Cybercriminals can use Remote Desktop Protocol (RDP) to gain administrative access to the front door, using a brute-force method of trying various passwords (dictionary attack) or they can use stolen credentials purchased on the Dark Web. Even the strongest password can be compromised via brute-force attack. Encryption.

Lenny Zeltser
JULY 25, 2018
In a modern twist, the scammer includes personal details about the recipient—beyond merely the person’s name—such as the password the victim used: “ is one of your password and now I will directly come to the point. We are preparing a lawsuit against the company that allowed a big data leak.

Thales Cloud Protection & Licensing
OCTOBER 23, 2023
Operational Technology (OT) systems, which were once isolated, have progressively integrated with IT technology and moved to various cloud platforms powered by sophisticated IoT sensors and guided by big data analytics. A Very Human Problem When tackling these security challenges, the human element is the most important factor.

eSecurity Planet
JANUARY 28, 2021
Its patent-pending Side-Scanning technology uses environmental context to prioritize risks, including vulnerabilities, misconfigurations, malware, compromised passwords and more. The company’s offering places it in a prime spot as the adoption of cloud computing continues to grow. A leak of highly sensitive Samsung source code.

The Last Watchdog
OCTOBER 18, 2021
MFA, also called two-factor authentication or 2FA, can help safeguard your data. It requires employees to log in to their multiple accounts using a handful of steps rather than just a username and password. About the essayist: April Miller is a staff writer at ReHack Magazine.

eSecurity Planet
DECEMBER 19, 2023
As organizations quickly adopt technologies like Okta Fastpass which uses biometrics for authentication instead of passwords, … we expect an increase in two areas: breaches caused by social engineering (already on the rise), and breaches caused by Insiders (already over 40% of all breaches).

Thales Cloud Protection & Licensing
FEBRUARY 22, 2018
Remember earlier this year when news broke that Hawaii’s Emergency Management Agency was keeping their passwords on a Post-it note, right after a false missile alert was blasted to residents across the state? citizens’ personal data being made available to the public, which has heightened awareness with government officials.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content