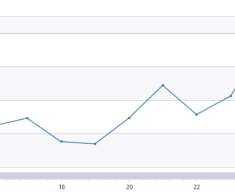
The activity of the Linux XorDdos bot increased by 254% over the last six months
Security Affairs
MAY 20, 2022
XorDdos leverages persistence mechanisms, efficient evasion, and anti-forensic techniques, including obfuscating the malware’s activities, evading rule-based detection mechanisms, and hash-based malicious file lookup. Microsoft experts observed in the last six months a 254% increase in the activity associated with XorDdos. .















Let's personalize your content