Stay on target: How accurate threat detection leads to better defense
Cisco Security
MARCH 9, 2022
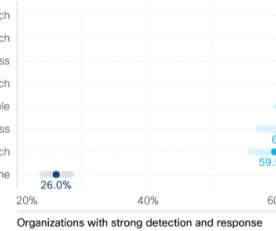
It also raises this big question: how exactly can enhanced visibility increase our chances of guarding against data breaches and attacks? Here, in part four of our five-part blog series , we’ll be focusing on that very question. People, processes, and technology: The cybersecurity trinity. Automate to protect.


















































Let's personalize your content