Data Scanning: How to Protect Sensitive & Confidential Data
Digital Guardian
DECEMBER 27, 2023
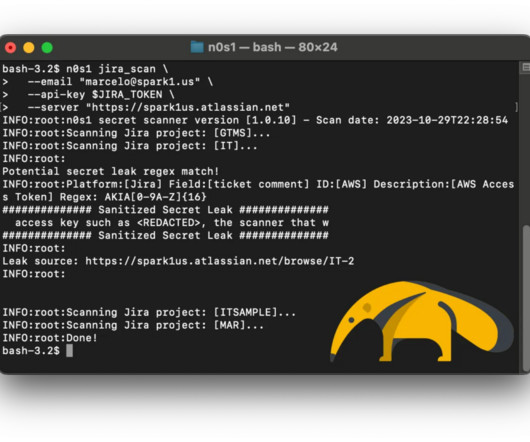
Being able to scan your data can give you the full scope of where files exist and what needs to be properly secured. In this blog, we break down why it's a key part of data loss prevention, who uses data scanning, and why it's important.
























Let's personalize your content