Updating Software: Learn the Importance of Keeping Up-to-Date With the Latest Software Version and Patches
Duo's Security Blog
OCTOBER 25, 2023
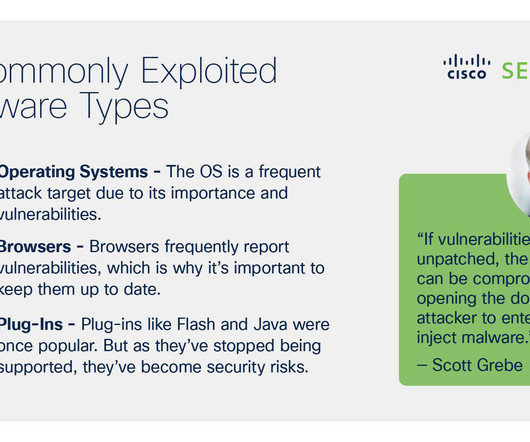
Outdated software in particular can be exploited due to vulnerabilities and bugs in the code. If the vulnerabilities go unpatched, the device can be compromised, opening the door for an attacker to enter and inject malware. For example, in 2022 SecurityWeek reported on 456 vulnerabilities in Google Chrome including nine zero-days.












Let's personalize your content