The Essential Role of Virtual Compliance Officers in Modern Business
Centraleyes
MAY 13, 2024
Decision-makers often grapple with the challenge of seeing cybersecurity not merely as a protective measure but as a revenue-generating asset. The intangible nature of cybersecurity measures adds complexity to this perception, making it challenging to quantify the immediate financial returns.








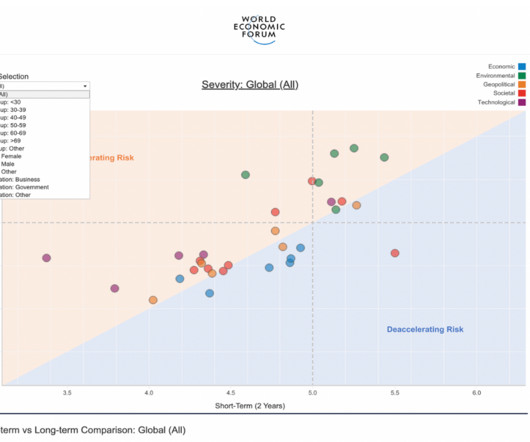



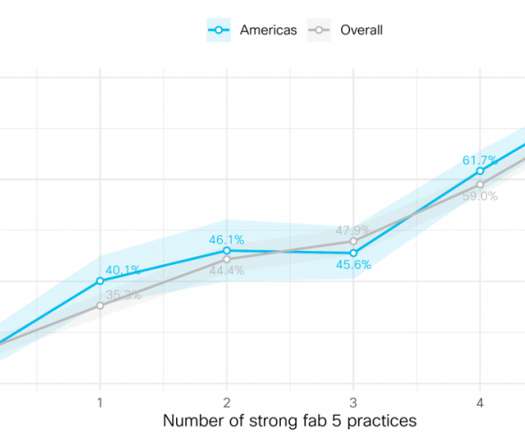

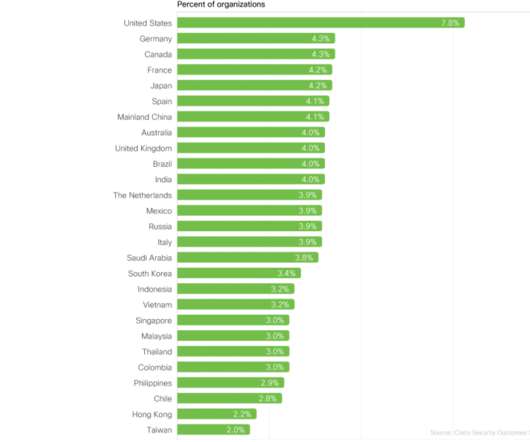










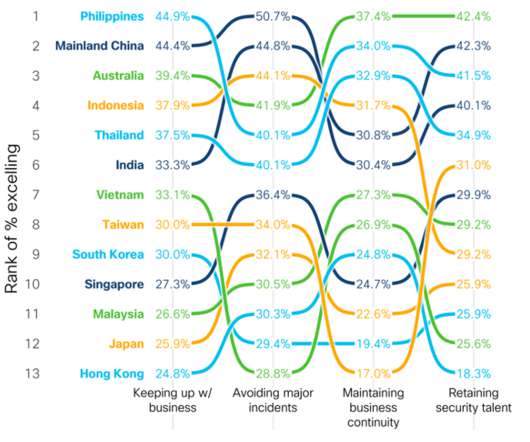


























Let's personalize your content