Colonial Pipeline, Darkside and Models
Adam Shostack
MAY 15, 2021
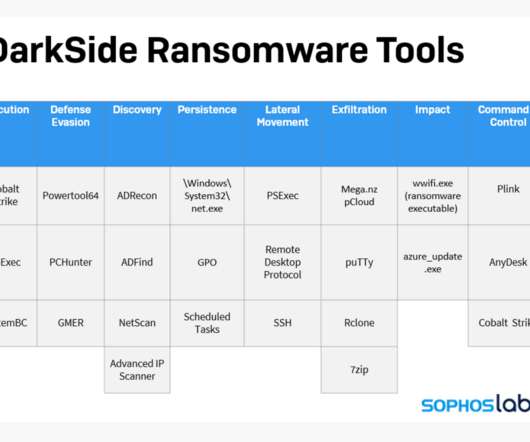
Blog posts from Sophos and Mandiant seem really useful! Move Laterally. Lateral Movement. For move laterally, Mandiant lists: Beacon, RDP, plink, F-Secure C3, while Sophos lists PSExec, RDP, SSH. I did want to talk about one small aspect, which is the way responders talk about Darkside. Initial Compromise.



















Let's personalize your content