All Customer Support System Users Exposed in The Okta Data Breach
Heimadal Security
NOVEMBER 29, 2023
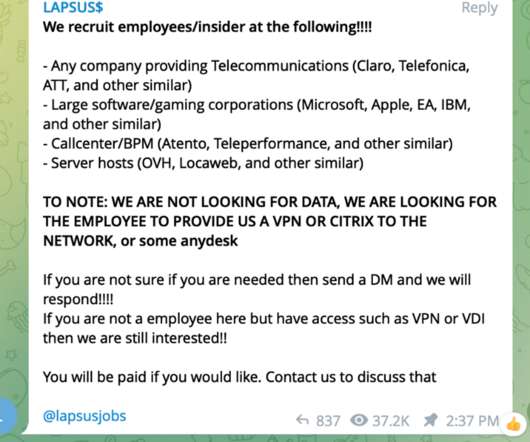
The ongoing Okta data breach investigation brings new details to light. The company announced that hackers have accessed data from every user of Okta’s customer support system.
















Let's personalize your content