How to Conduct a Successful Privileged Access Management Audit
Heimadal Security
NOVEMBER 17, 2023
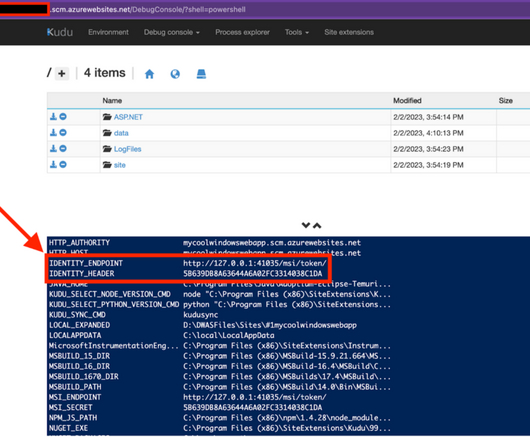
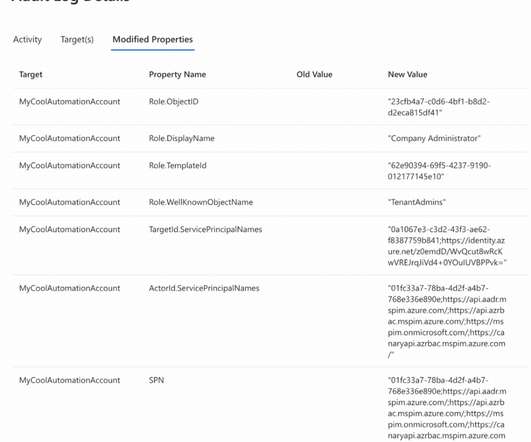
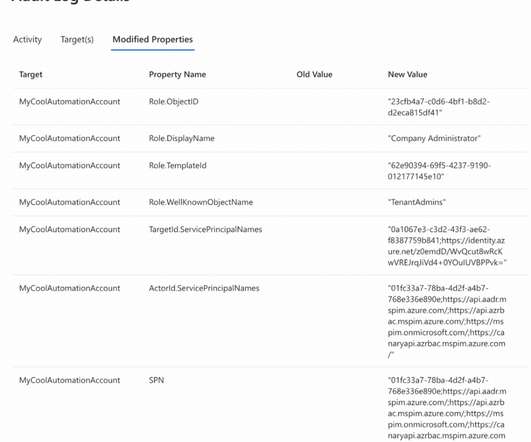
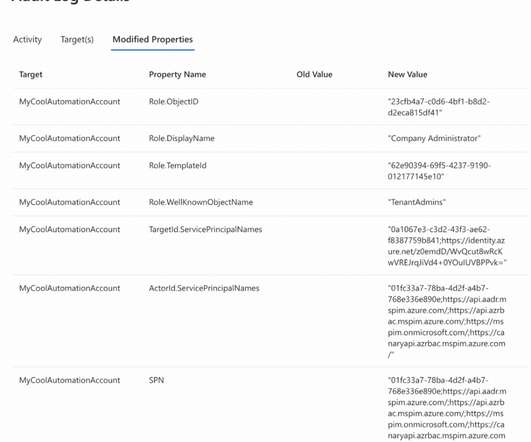
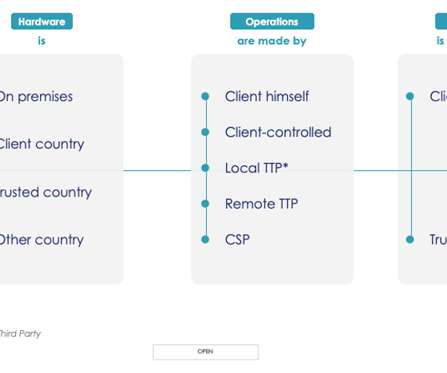
As we’ve already established in our previous article, the ‘privilege overreach’ phenomenon can pose a serious security risk, which could lead to data breaches, operational downtime, and financial losses. This threat demands more than just awareness; it requires a strategic and thorough response.










































Let's personalize your content