The Russia-linked APT29 is behind recent attacks targeting NATO and EU
Security Affairs
APRIL 13, 2023
Poland’s Military Counterintelligence Service and its Computer Emergency Response Team linked a recent string of attacks targeting NATO and European Union countries to the Russia-linked APT29 group (aka SVR group , Cozy Bear , Nobelium , and The Dukes ).


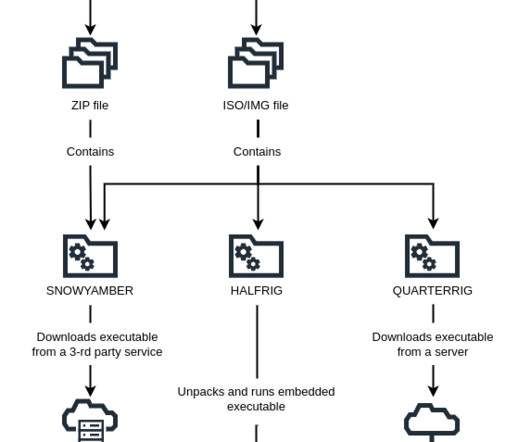
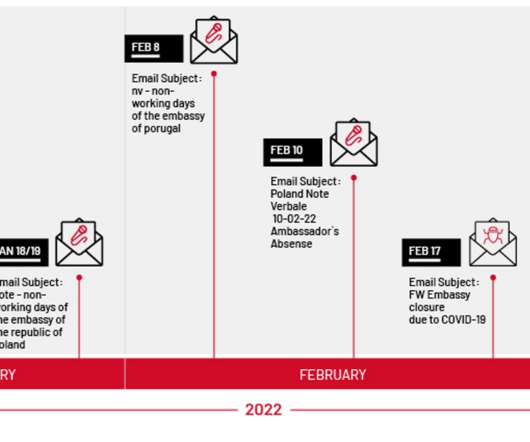


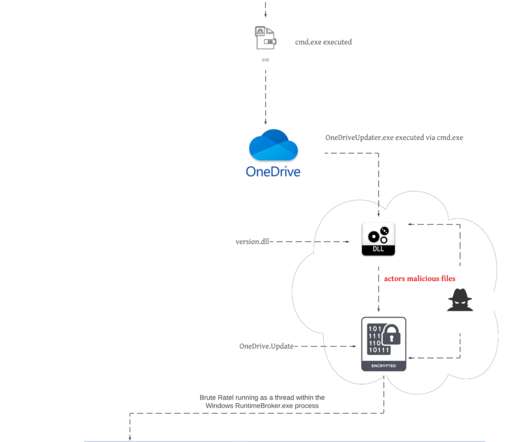








Let's personalize your content