What Is Token-Based Authentication?
Heimadal Security
SEPTEMBER 11, 2023
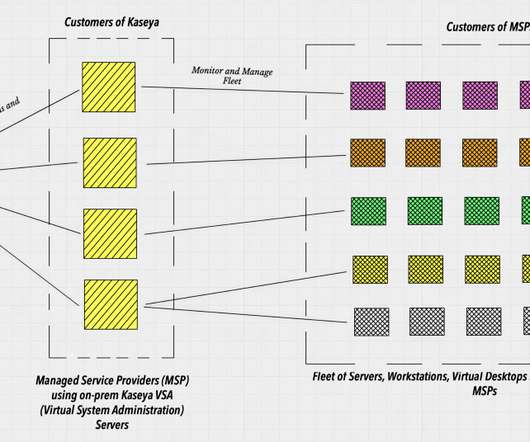
Secured authentication to databases and systems is essential to enterprise cybersecurity management. Fortunately, there’s an approach that guarantees security without the vulnerabilities […] The post What Is Token-Based Authentication? appeared first on Heimdal Security Blog.















































Let's personalize your content