RFID: Is it Secret? Is it Safe?
Approachable Cyber Threats
JULY 19, 2022
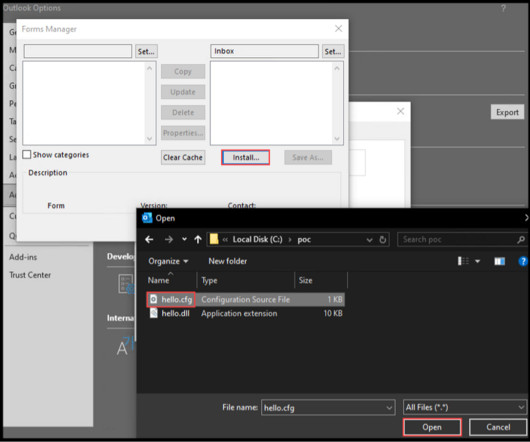
Other common use cases you may be familiar with are when you badge into a physical location such as a hotel room, a secure office building or floor in an office building, an apartment or condo complex, or maybe a dorm or school building on a college campus. In fact, it’s been around since the 1940s.

































Let's personalize your content