The people problem: Large businesses shift resources to address risks tied to new and disgruntled employees
SC Magazine
MARCH 11, 2021
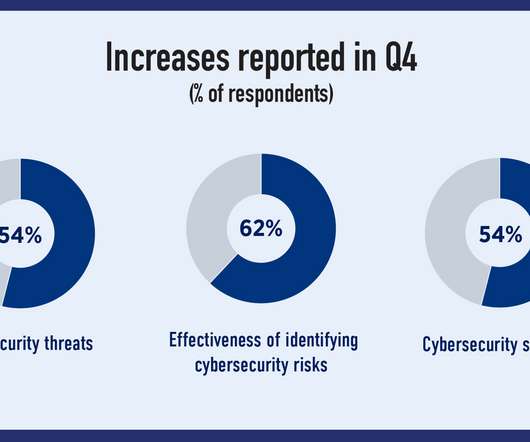
The lasting impact of 2020 on cybersecurity has come more clearly into relief, as security professionals reported more mature, effective strategies and approaches spanning threat prevention, detection and response – with many businesses reallocating resources to address risks tied to the workforce.























Let's personalize your content