Third-party risk considerations associated with the Executive Order
Security Boulevard
JUNE 14, 2021
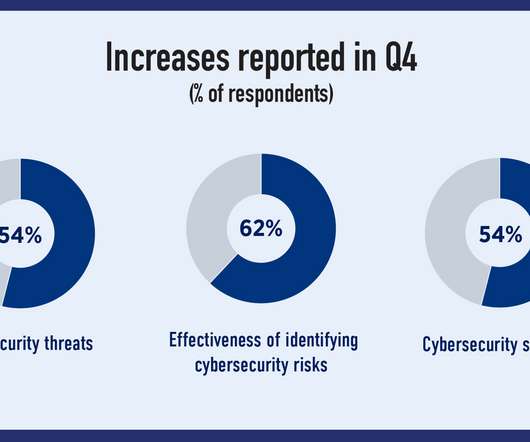
For providers of technology and business services, like value added resellers (VARs) and managed service providers (MSPs), it’s important to acknowledge a customer’s risk of third-party cyberattacks – especially because VARs and MSPs are likely one of those third-party connections.























Let's personalize your content