Log4Shell: The New ‘Heartbleed’
Approachable Cyber Threats
DECEMBER 16, 2021
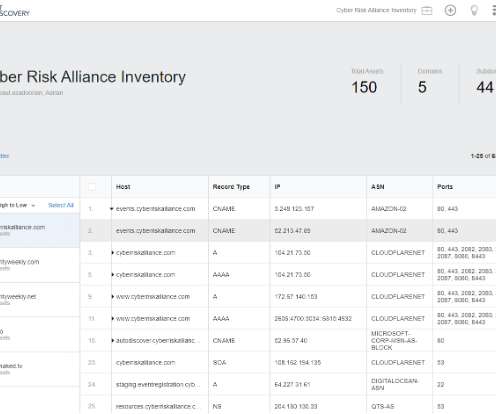
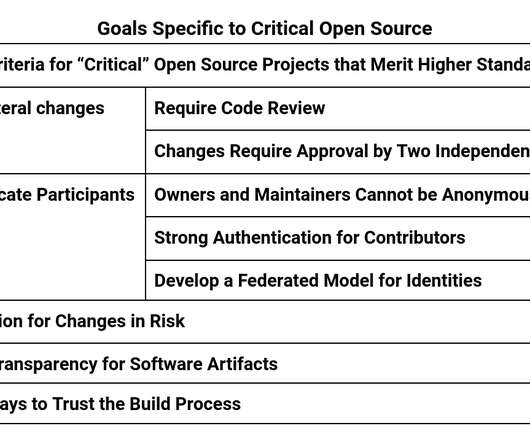
Category News, Vulnerabilities Risk Level. Log4j is an open source, Apache maintained Java-logging library that is used across the globe in popular applications and services. Log4j was developed to provide a Java logging framework to standardize the process of logging on the Java platform. What is Log4j?”


































Let's personalize your content