Cybersecurity Snapshot: Experts Issue Best Practices for Migrating to Post-Quantum Cryptography and for Improving Orgs’ Cyber Culture
Security Boulevard
JUNE 6, 2025
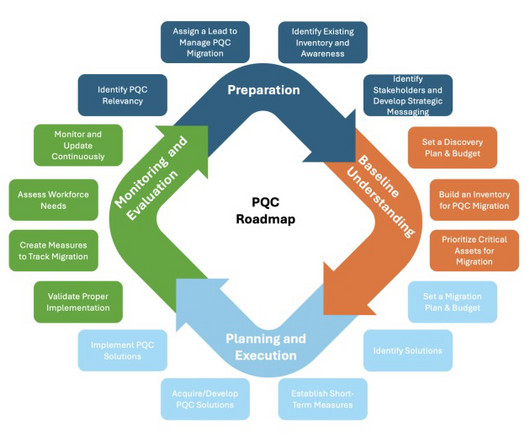
And get the latest on exposure response strategies and on CISO compensation and job satisfaction. National Institute of Standards and Technology (NIST) released three quantum-resistant algorithm standards in 2024 and expects to release a fourth in 2026. Plus, find out how your company can create a better cybersecurity environment.

























Let's personalize your content