How To Set Up a Firewall in 8 Easy Steps + Best Practices
eSecurity Planet
APRIL 30, 2024
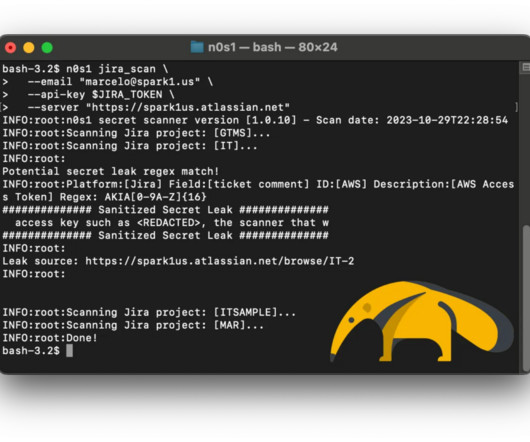
Setting up a firewall is the first step in securing your network. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively improve your network integrity and data security. Take note of your security requirements, physical environment, and component interoperability.



























Let's personalize your content