Top 5 Cyber Attack news headlines trending on Google
CyberSecurity Insiders
JUNE 14, 2021
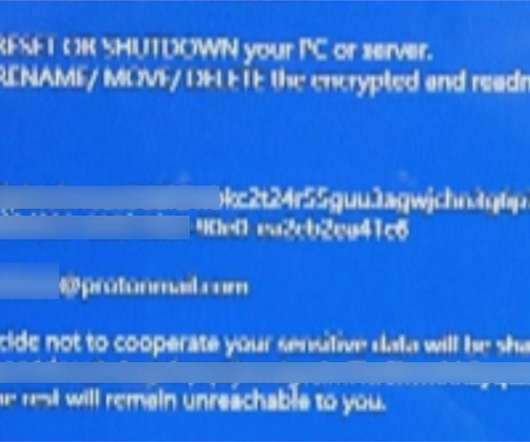
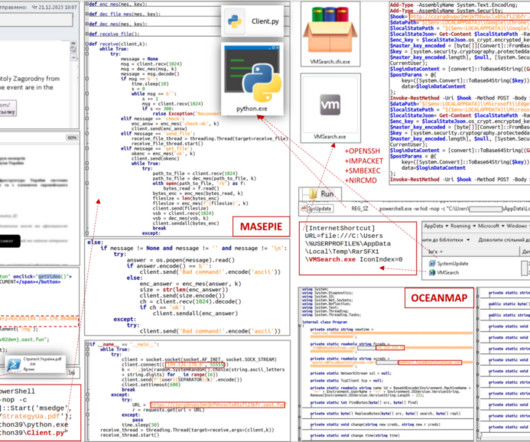
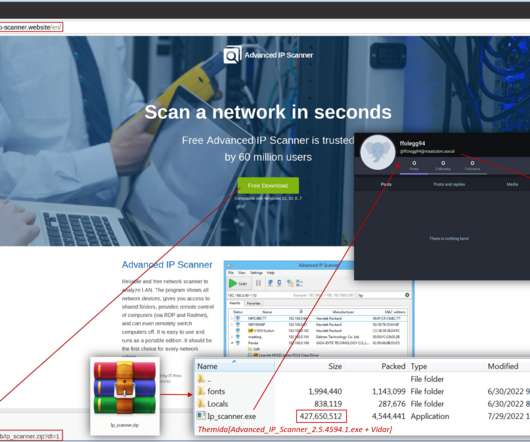
The 45-year old has reportedly taken part in the attack that disrupted phone services and network printer services related to the healthcare services provider to obtain information for later selling it online for monetary benefits. The post Top 5 Cyber Attack news headlines trending on Google appeared first on Cybersecurity Insiders.















































Let's personalize your content