Cryptocurrency Phishing Threats Luring New Victims
Security Boulevard
APRIL 14, 2023
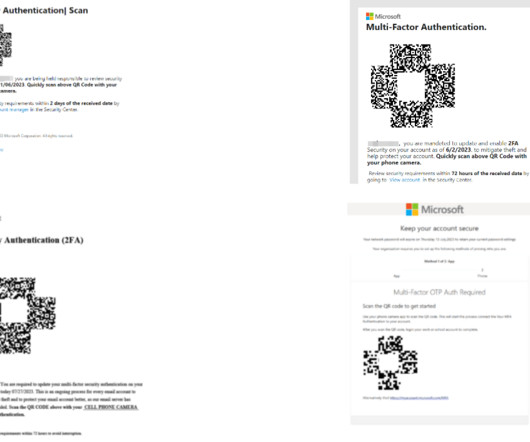
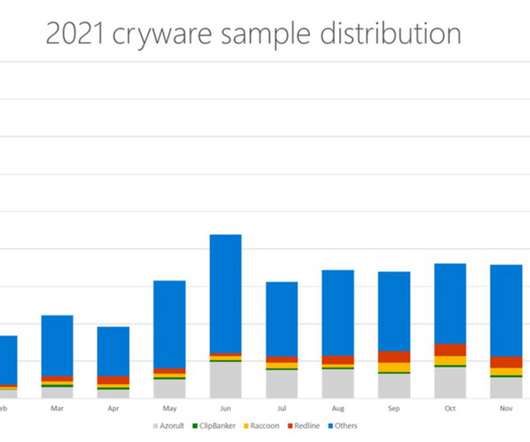
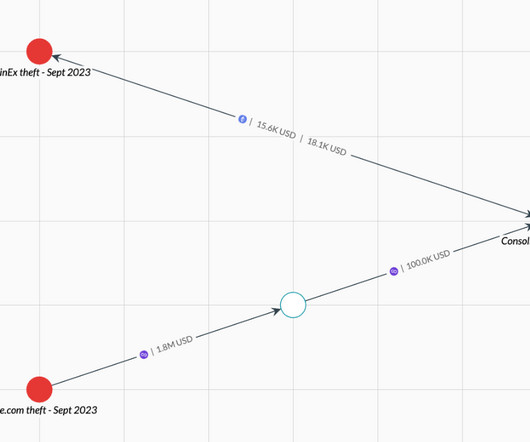
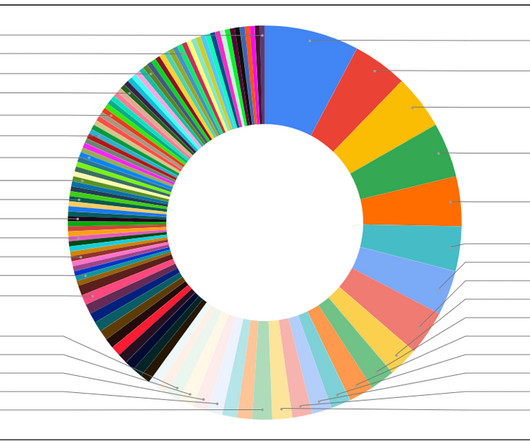
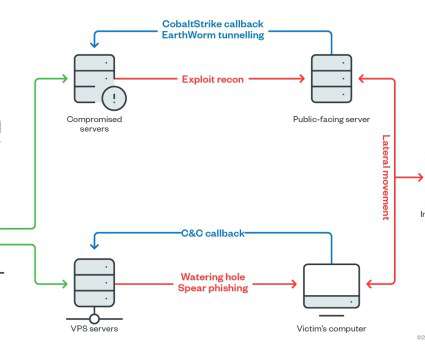
Cryptocurrency-related phishing attacks are on the rise, with a report from Kaspersky recording an increase of 40% in 2022 compared to the previous year. The post Cryptocurrency Phishing Threats Luring New Victims appeared first on Security Boulevard.














































Let's personalize your content