U.S. Internet Leaked Years of Internal, Customer Emails
Krebs on Security
FEBRUARY 14, 2024
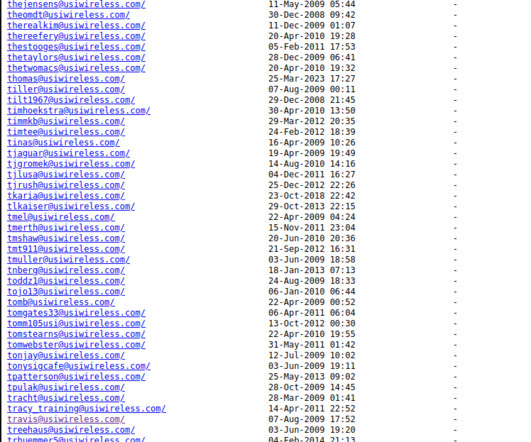
A tiny portion of the more than 6,500 customers who trusted U.S. Securence counts among its customers dozens of state and local governments, including: nc.gov — the official website of North Carolina; stillwatermn.gov , the website for the city of Stillwater, Minn.; Internet with their email.














































Let's personalize your content