These are the sources of DDoS attacks against Russia, local NCCC warns
Security Affairs
MARCH 4, 2022
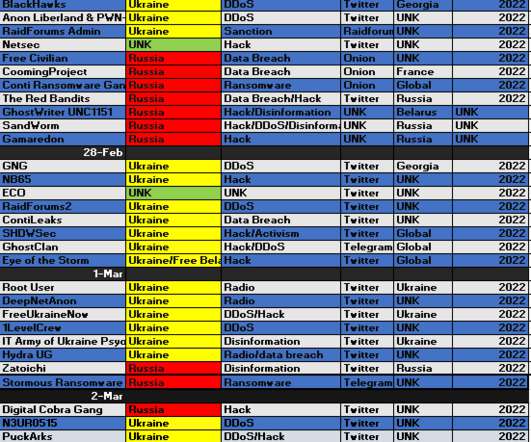
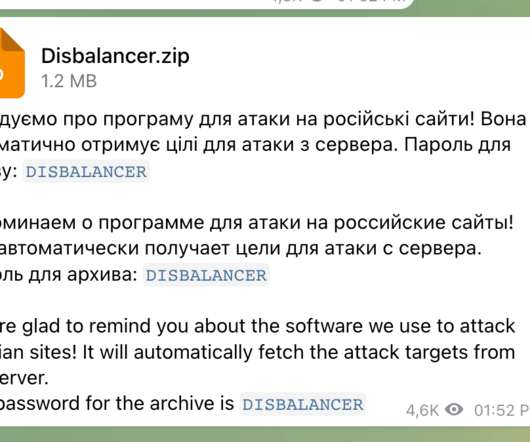
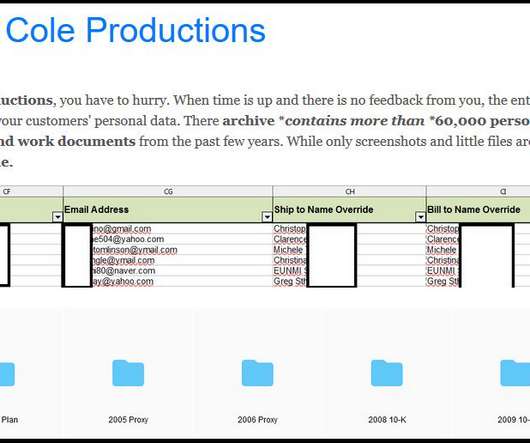
Russian government released a list containing IP addresses and domains behind DDoS attacks that hit Russian infrastructure after the invasion. SecurityAffairs – hacking, DDoS). The post These are the sources of DDoS attacks against Russia, local NCCC warns appeared first on Security Affairs. Pierluigi Paganini.







































Let's personalize your content