New Cyber Attack Campaign Leverages the COVID-19 Infodemic
Security Affairs
FEBRUARY 26, 2020
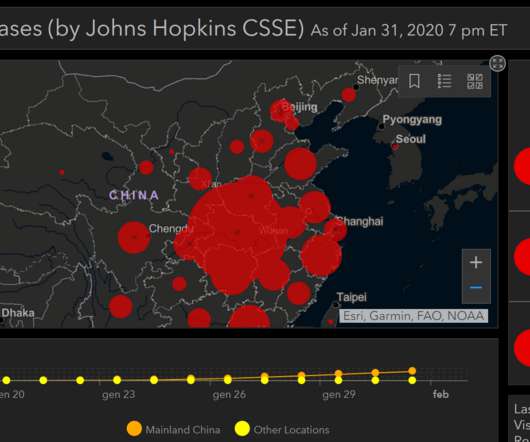
Nowadays, it is common to say that the physical world and the cyber world are strictly connected. The proof is the leverage of the current physical threat, the CoronaVirus (COVID-19), as a social engineering trick to infect the cyber world. gripe”, possibly to avoid reputation warnings raised by next-gen firewalls.





















Let's personalize your content