NEW TECH: Trend Micro flattens cyber risks — from software development to deployment
The Last Watchdog
AUGUST 25, 2020
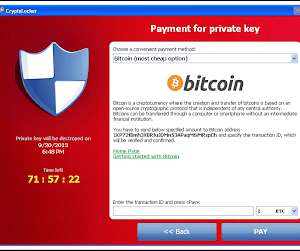
Covid19 has upgraded the Internet — from the criminals’ point of view — to a picture-perfect environment for phishing, scamming and deep network intrusions. Thus the urgency for organizations to put all excuses aside and embrace stricter cyber hygiene practices could not be any higher. I’ll keep watch.






































Let's personalize your content