Third-Party Cyber-Risk by the Numbers
Dark Reading
APRIL 19, 2019
Recent stats show that the state of third-party cyber-risk and vendor risk management remains largely immature at most organizations.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 third-party-cyber-risk-by-the-numbers
third-party-cyber-risk-by-the-numbers  Cyber Risk Related Topics
Cyber Risk Related Topics 
Dark Reading
APRIL 19, 2019
Recent stats show that the state of third-party cyber-risk and vendor risk management remains largely immature at most organizations.

The Last Watchdog
JULY 13, 2023
London, July 13, 2023 — Beazley, the leading specialist insurer, today published its latest Risk & Resilience report: Spotlight on: Cyber & Technology Risks 2023. Yet, boardroom focus on cyber risk appears to be diminishing. trillion by 2025, a 300% increase since 2015 1.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 2, 2022
Third-Party Risk Management ( TPRM ) has been around since the mid-1990s – and has become something of an auditing nightmare. Related: A call to share risk assessments. This is because third-party risk has become a huge problem for enterprises in the digital age. One leading provider is Denver, Colo.-based

SecureWorld News
OCTOBER 20, 2021
Cyberrisk is business risk. But how should we communicate this risk to the business, to clients, or to investors? For an increasing number of companies, part of that conversation is happening in quarterly and annual reports. Accenture annual report: risks we face from cyberattacks. For example, company earnings hit $50.5

CyberSecurity Insiders
OCTOBER 11, 2022
By knowing just how big your digital footprint is you’ll be in a better position to guard your business against cyber incursion. . Contact details containing email addresses, chat options, or telephone numbers taking customers through to an IVR (interactive voice response) service will all be there on the net. .

Centraleyes
FEBRUARY 13, 2024
Categorizing risks as high, medium, or low has been the go-to method for organizations seeking to prioritize their cybersecurity efforts. Ten Risks in a Bed Remember the nursery rhyme? Ten Risks in a Bed Remember the nursery rhyme? Enter the need for a more precise and actionable approach — Cyber Risk Quantification.

SecureWorld News
APRIL 29, 2024
While Kaiser has not provided many specifics about the nature of the cybersecurity incident, the company stated that the compromised data included individuals' names, addresses, email addresses, and may have also included medical information and health record numbers depending on the person. in terms of the number of people impacted.

The Last Watchdog
DECEMBER 5, 2018
million patients had significant amounts of PII exposed by the healthcare provider’s third-party billing vendor, AccuDoc Solutions, shows the healthcare sector remains acutely vulnerable to attacks exploiting third-party contractors even as their first-party security posture hardens. Weak links. Sticky problem.

CyberSecurity Insiders
JULY 3, 2022
A cyber gang has leaked data of thousands of British school pupils online and is also threatening to add more to the list, as almost all the 6 victims have chosen not to entertain the cyber criminals. However, none of them responded to the group of cyber criminals positively and so it sold the siphoned data on the web.

CyberSecurity Insiders
MARCH 7, 2021
The increasing number of third-party data breaches and the sensitive information they expose have negatively impacted consumer trust. Third-party breaches occur when sensitive data is stolen from a third-party vendor or when their systems are used to access and steal sensitive information stored on your systems. .

Adam Levin
JULY 16, 2018
The personal data for up to 14 million Verizon customers was discovered on an unprotected web server in late June by a cyber risk researcher. ” Dan O’Sullivan of UpGuard, a cybersecurity company, also expressed concern, stating that the exposure was a “remarkable incidence of third-party vendor risk.

Security Affairs
DECEMBER 1, 2022
Eliminating the risk of a data breach is nearly impossible, but some things can be done to reduce it significantly. Yahoo initially reported that 1 billion users had been affected, but the number turned out to be much higher. Data breaches can be devastating for organizations and even entire countries. SolarWinds attack on U.S.

SecureWorld News
MAY 27, 2021
A new security audit reveals that cyber bad actors hit the National Aeronautics and Space Administration (NASA) with more than 6,000 attacks during the last four years. The Agency's cybersecurity challenges are further exacerbated by the number and variety of IT devices at NASA and the sheer volume of data the Agency maintains.".

eSecurity Planet
MAY 27, 2021
The explosion of ransomware and similar cyber incidents along with rising associated costs is convincing a growing number of insurance companies to raise the premiums on their cyber insurance policies or reduce coverage, moves that could further squeeze organizations under siege from hackers. Insurers Assessing Risks.

eSecurity Planet
MAY 3, 2022
The Attack Surface Management team at Group-IB said it constantly scans the IPv4 landscape for exposed databases, potentially unwanted programs, and other risks. The Attack Surface Management team at Group-IB said it constantly scans the IPv4 landscape for exposed databases, potentially unwanted programs, and other risks.

The Last Watchdog
FEBRUARY 3, 2020
Department of Homeland Security issued a bulletin calling out Iran’s “robust cyber program,” and cautioning everyone to be prepared for Iran to “conduct operations in the United States.” ” Related: Cyber warfare enters Golden Age In fact, strategic cyber operations essentially pitting Russia and Iran against the U.S.

Adam Levin
JULY 3, 2019
The situation at this third- and sometimes fourth-party debt collection agency was ongoing. As a third-party vendor to a HIPAA covered entity, AMCA would almost certainly be subject to the requirements of the HIPAA Privacy, Security, Enforcement, and Breach Notification Rules. This epic cybersecurity fail was avoidable.

eSecurity Planet
APRIL 22, 2022
That’s where cyber insurance may be able to help. As the number and severity of data breaches continues to rise, organizations are recognizing that those costs are not theoretical. However, a good cyber insurance provider can also leverage their partnerships to help your company afford better security controls. That’s a 29.1%

Security Boulevard
DECEMBER 6, 2023
The proliferation of attacks - 66% of organizations were hit in the past year - and the ability for threat actors to more easily execute these attacks at scale, makes ransomware “ arguably the biggest cyber risk facing organizations today.” Vulnerability exploits are the most common root cause of ransomware attacks.

CyberSecurity Insiders
OCTOBER 23, 2021
The report provides an inside look at the insights and tools used by risk managers, IT departments, security researchers, and solution providers to hone their offerings and approaches to keeping organizations safe from evolving cyber threats. “By Ransomware claims and costs.

SC Magazine
FEBRUARY 8, 2021
While 80% of the 1,500 technology and procurement chiefs surveyed by BlueVoyant had experienced at least one breach caused by a third-party vendor 12 months prior, most (anywhere from 71% to 81%, depending on the industry) don’t monitor all third-party suppliers for cyber risk.

The Last Watchdog
OCTOBER 10, 2019
Related: Implications of huge Capital One breach CASBs supplied a comprehensive set of tools to monitor and manage the multitude of fresh cyber risks spinning out of the rise in in corporate reliance on cloud services. In doing so, CASBs became the fastest growing security category ever , as declared by Gartner.

McAfee
NOVEMBER 3, 2020
There are new and expanding opportunities for women’s participation in cybersecurity globally as women are present in greater numbers in leadership. Forrester also predicts that the number of women CISOs at Fortune 500 companies will rise to 20 percent in 2019 , compared with 13 percent in 2017. Live Panel. Can’t make it?

Security Boulevard
JUNE 8, 2021
By Sam Jones | Cyber Tec Security. It’s important to remember, however, as we slowly transition back into some semblance of normality, that there will be new challenges to face in all facets of life, and the Cyber Security sector is no exception.

The Last Watchdog
MARCH 29, 2022
based networking systems supplier, like any number of other established tech giants, as well as innumerable cybersecurity startups, is deeply vested in seeing this transition through to the end. Log4j is the latest, greatest vulnerability to demonstrate just how tenuous the security of modern networks has become. The Sunnyvale, Calif.-based

eSecurity Planet
FEBRUARY 11, 2022
It’s an excellent asset for cyber defense, but adversaries have learned to trick algorithms and even use similar technology to compromise targeted systems. ML for Cyber Defense. Machines can recognize patterns to detect malware and unusual activity better than humans and classic software. ML uses experience to improve its tasks.

SecureWorld News
JANUARY 6, 2021
The lawsuit refers to financial reports that SolarWinds filed while the cyber actors had access to it's systems. In addition things listed here, some third-parties have come forward to say they tried to warn SolarWinds of its potential cyber risks, but those warnings were allegedly ignored by the company.

Security Affairs
APRIL 29, 2019
A cyber survey conducted by the United Kingdom’s National Cyber Security Centre (NCSC) revealed that ‘123456’ is still the most hacked password. This data is disconcerting and shows that we are far from to be secure even if security experts continue to warn users of cyber risks associated with the use of weak passwords.

CyberSecurity Insiders
NOVEMBER 26, 2021
It’s safe to say that 2021 has been a challenging yet rewarding year for those working to ensure cyber security systems provide protection. Perhaps now is a good time to reflect on how firms have tackled the existential challenge of increasing cyber risks in a rapidly changing online landscape.

eSecurity Planet
JANUARY 5, 2023
After a year that saw massive ransomware attacks and open cyber warfare, the biggest question in cybersecurity for 2023 will likely be how much of those attack techniques get commoditized and weaponized. 2023, he predicted, “will not be any easier when it comes to keeping users’ data safe and private.” Trade Cyberthreats.

IT Security Guru
FEBRUARY 28, 2022
Given the connectivity needs of a remote workforce – and knowing a hybrid workforce is here to stay – many IT teams have had to make sudden changes in the way workers connect to corporate systems that could introduce new cyber risks and vulnerabilities. . Security landscape requires adaptation .

SC Magazine
FEBRUARY 18, 2021
Weak passwords and developer misconfigurations consistently lead to source code leaks from third-party repositories, even at large companies with robust security programs, such as Nissan North America. Risks associated with intellectual property leaks are not limited to the automotive industry. Common developer mistakes.

Security Affairs
APRIL 13, 2023
Knowing that insider threats are a risk is one thing. Dealing with issues of insider cyber risk can be different and nuanced. However, over one-third of businesses are impacted by insider threats every year, and US businesses face about 2.500 internal security breaches in the aggregate per day. These cases are out there.

Security Affairs
JANUARY 19, 2022
“This CISA Insights is intended to ensure that senior leaders at every organization in the United States are aware of critical cyber risks and take urgent, near-term steps to reduce the likelihood and impact of a potentially damaging compromise. . ” reads the insights” document. ” reads the insights” document.
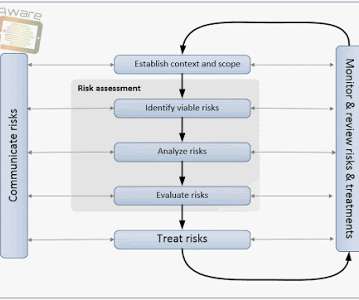
Notice Bored
APRIL 22, 2021
After all, an ISO27k ISMS is, essentially, simply a structured, systematic approach for information risk management, isn't it? Types and significances of risks – different threats, vulnerabilities and impacts, different potential incidents of concern; Understandings of ‘information’, ‘risk’ and ‘management’ etc.

eSecurity Planet
FEBRUARY 11, 2022
Risk management is a concept that has been around as long as companies have had assets to protect. Risk management also extends to physical devices, such as doors and locks to protect homes and vehicles, vaults to protect money and precious jewels, and police, fire, and CCTV to protect against other physical risks.

Security Affairs
JANUARY 14, 2019
The huge trove of data belongs to job seekers in China, its records include personal information of individuals like names, height, weight, email IDs, marriage status, political leanings, skills and work experience, phone numbers, salary expectations, and driver licenses were exposed. Pierluigi Paganini.

IT Security Guru
DECEMBER 9, 2020
Instead, it had been discovered that one of their software providers had not stored sensitive data correctly, running the risk that the details of millions of hotel customers could have been exposed. million following a cyber attack in 2018 which flagged that it was failing to keep its customers’ personal data secure.

SecureWorld News
JUNE 30, 2021
It is not very often that a ransomware attack can actually cause physical harm to a person. We have seen it a few times during the pandemic, with cybercriminals targeting the healthcare sector to steal information on anything related to COVID-19. Now, we are seeing it again with a ransomware attack that targeted Scripps Health.

SecureWorld News
JUNE 30, 2021
It is not very often that a ransomware attack can actually cause physical harm to a person. We have seen it a few times during the pandemic, with cybercriminals targeting the healthcare sector to steal information on anything related to COVID-19. Now, we are seeing it again with a ransomware attack that targeted Scripps Health.

SC Magazine
JULY 8, 2021
Devon Ackerman, managing director and head of incident response for North America with Kroll’s Cyber Risk practice, said that the malicious actors behind this growing trend are “directly tied to ransomware groups” and are likely using automated scripts to seek out “Contact Us” or chat forms on the internet that they can abuse.

SecureWorld News
FEBRUARY 4, 2021
Our family came home from a New Year's Eve party, and when we opened the door from the garage into the house, we just knew. Here's the twist: the Sheriff's department told us this was the third time our house had been broken into through the same point of entry. Burglars had ransacked the place. That's excellent advice.

Security Boulevard
APRIL 1, 2022
and has become more central to trust for a variety of features and services such as SafetyNet, Identity Credential, Digital Car Key, and a variety of third party libraries, according to Google. “In Attestation has been mandated since Android 8.0 Why the change? This will now be done by Remote Key Provisioning. Remote Provisioning.

Thales Cloud Protection & Licensing
JUNE 15, 2023
A third-party service provider manages a KMaaS solution to alleviate the burden of cryptographic key management. By using a cloud-based KMaaS provider, organizations can centralize and automate their key lifecycle management, reducing the risk of inconsistent policies or compromised keys.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content