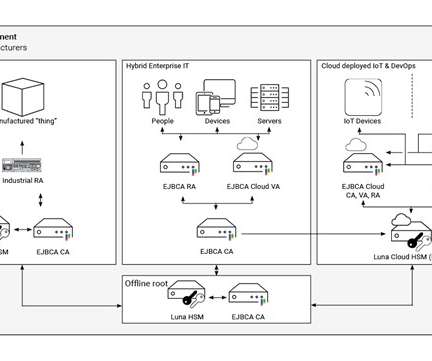
Manufacturing needs to adopt a Zero Trust approach to mitigate increased cyber threats
Thales Cloud Protection & Licensing
OCTOBER 19, 2022
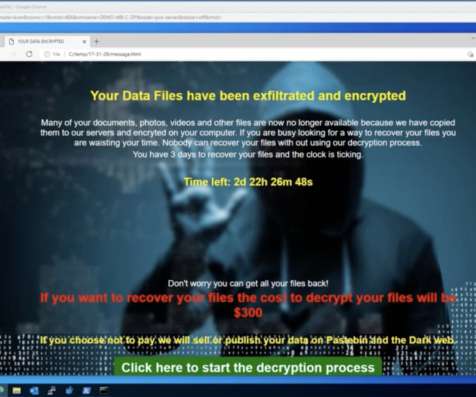
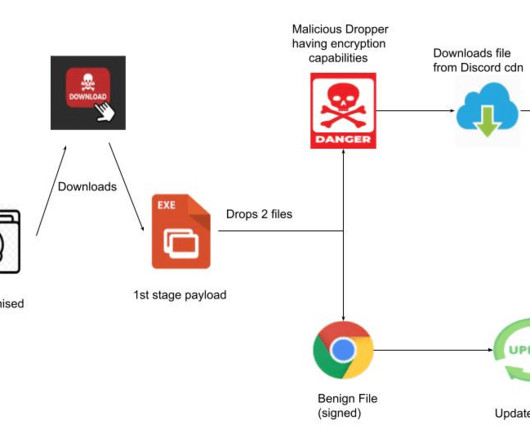
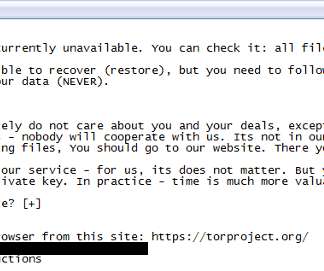
Manufacturing needs to adopt a Zero Trust approach to mitigate increased cyber threats. Long gone is the time when manufacturing systems and operations were siloed from the Internet and, therefore, were not a cybersecurity target. Thu, 10/20/2022 - 06:20. Survey’s key findings.















































Let's personalize your content