Handling Pandemic-Scale Cyber Threats (preprint)
Adam Shostack
JANUARY 2, 2025
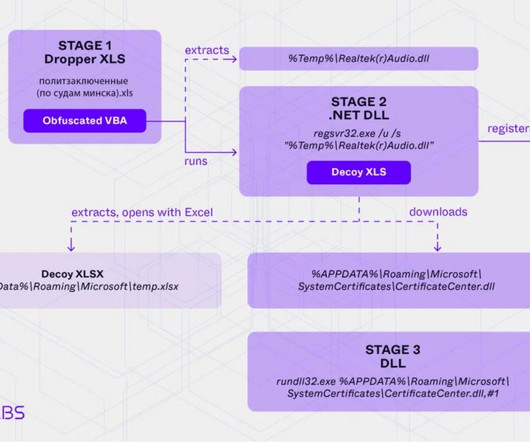
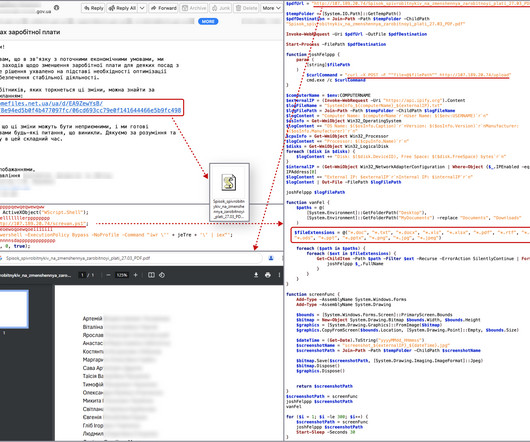
A new paper on 'Pandemic Scale Cyber Events Josiah Dykstra and I have a new pre-print at Arxiv, Handling Pandemic-Scale Cyber Threats: Lessons from COVID-19. While the nature of these threats differs, the responses to COVID-19 illustrate valuable lessons that can guide preparation and response to cyber events.
















































Let's personalize your content