News Alert: Criminal IP unveils innovative fraud detection data products on Snowflake Marketplace
The Last Watchdog
JUNE 10, 2024
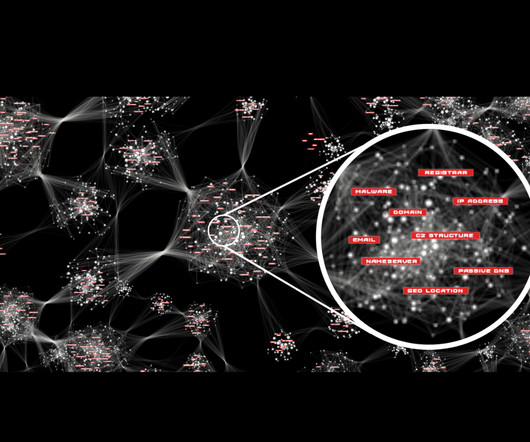
June 10, 2024, CyberNewsWire — AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced that it has started selling its paid threat detection data from its CTI search engine ‘ Criminal IP ‘ on the Snowflake Marketplace. Torrance, Calif., About AI Spera.

















































Let's personalize your content