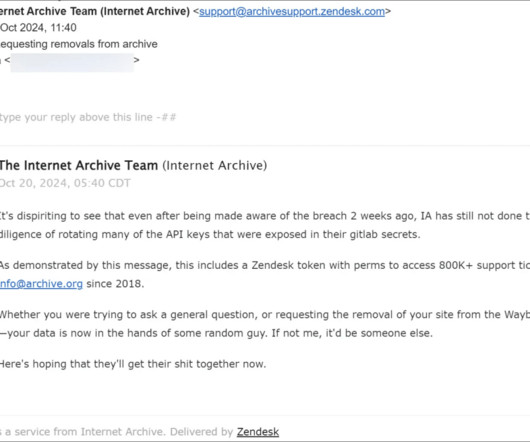
Cisco states that data published on cybercrime forum was taken from public-facing DevHub environment
Security Affairs
OCTOBER 21, 2024
Cisco confirms that data published by IntelBroker on a cybercrime forum was taken from the company DevHub environment. Cisco confirms that the data posted by IntelBroker on a cybercrime forum was stolen from its DevHub environment. for customers to use as needed.



































Let's personalize your content