BianLian, White Rabbit, and Mario Ransomware Gangs Team Up for Mega-Extortion
Penetration Testing
DECEMBER 15, 2023
In the shadowy world of cybercrime, alliances are formed not in boardrooms, but in the encrypted corners of the dark web.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Penetration Testing
DECEMBER 15, 2023
In the shadowy world of cybercrime, alliances are formed not in boardrooms, but in the encrypted corners of the dark web.

SecureList
OCTOBER 20, 2021
Having been in the field for so long, we have witnessed some major changes in the cybercrime world’s modus operandi. This report shares our insights into the Russian-speaking cybercrime world and the changes in how it operates that have happened in the past five years. Conclusion: cybersecurity and cybercrime have matured.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
JANUARY 1, 2024
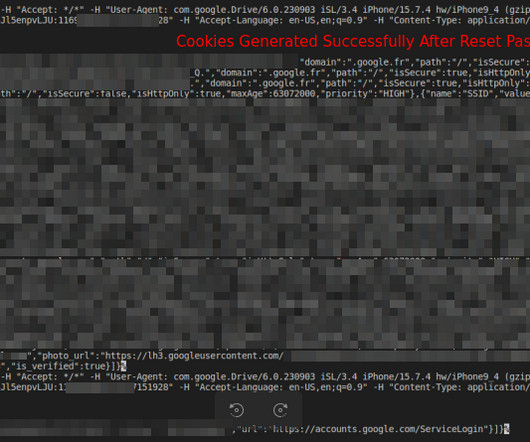
The encrypted tokens are decrypted using an encryption key stored in Chrome’s Local State within the UserData directory, similar to the encryption used for storing passwords.” The exploit’s imperfect testing led to revealing its source.” ” reads the report published by CloudSEK.

Hot for Security
APRIL 19, 2021
Notorious FIN7 gang stole payment card details from retailers around the world Cybercrime gang posed as penetration testing firm to recruit hackers. FIN7 operated a front company called Combi Security, which claimed to offer penetration testing services.

CyberSecurity Insiders
JANUARY 28, 2022
Encrypt Data at All Points. Another crucial step in securing health care data is encrypting it. HIPAA doesn’t necessarily require encryption, but it is a helpful step in maintaining privacy, as it renders information virtually useless to anyone who intercepts it. Penetration Test Regularly.

Security Affairs
MAY 9, 2021
At the end of April, researchers from FireEye’s Mandiant revealed that a sophisticated cybercrime gang tracked as UNC2447 has exploited a zero-day issue ( CVE-2021-20016 ) in SonicWall Secure Mobile Access (SMA) devices, fixed earlier this year, before the vendor addressed it.

SecureWorld News
FEBRUARY 27, 2021
One of the major issues surrounds keeping remote workers protected against cybercrime. Additionally, if you are only using a basic VPN, it can be sensible to upgrade your encryption to a Layer Two Tunneling Protocol (L2TP) , which offers better protection for businesses wanting to keep data secure. Test your own system.

SecureWorld News
OCTOBER 22, 2023
If you are already familiar with the evolving cyber threat landscape in your home country, you’ll know that humans are often the most exploited attack vector for cybercrime, and how frequently small businesses are breached. This secure information should be safeguarded in impenetrable servers with valid encryption protocols enabled.

Security Affairs
MARCH 19, 2020
” According to the experts, the first infections were observed in late 2019, victims reported their files were encrypted by a strain of malware. locked to the filename of the encrypted files. “On one of the compromised information systems, experts found encrypted files with the extension “ newversion.”

Security Affairs
JANUARY 28, 2023
The recent Hive infrastructure takedown as well as other major gangs dissolution such as Conti in 2022, is making room in the cybercrime business The Lockbit locker leaked a few months ago in the underground, is increasing its popularity and adoption among micro-criminal actors.

The Last Watchdog
JUNE 21, 2020
Although most people think of ransomware as a dodgy application that encrypts data and holds it for ransom, the concept is much more heterogeneous than that. File encryption 2013 – 2015. It emerged in September 2013 and paved the way for hundreds of file-encrypting menaces that have splashed onto the scene ever since.

Krebs on Security
FEBRUARY 16, 2022
The same day the ICRC went public with its breach, someone using the nickname “ Sheriff ” on the English-language cybercrime forum RaidForums advertised the sale of data from the Red Cross and Red Crescent Movement. This in turn allowed them to access the data, despite this data being encrypted.” ” On Jan.

The Last Watchdog
OCTOBER 5, 2023
He previously chronicled the emergence of cybercrime while covering Microsoft for USA TODAY. Byron: It’s gone from simple file encryption to multifaceted, multi-staged attacks that leverage Dark Web services, such as initial access brokers (IABs,) as well as make use of Living off the Land (LotL) embedded tools.

Security Affairs
APRIL 18, 2021
CARBANAK cybercrime gang was first uncovered in 2014 by Kaspersky Lab that dated its activity back to 2013 when the group leveraged the Anunak malware in targeted attacks on financial institutions and ATM networks. Starting from 2016 the group developed a new custom malware using Cobalt Strike, a legitimate penetration testing framework.

CyberSecurity Insiders
OCTOBER 14, 2021
Ransomware attacks like the ones carried out by OnePercent Group have been crippling businesses across the country since the FBI first reported a 37% uptick in cybercrime in 2018. Encrypt all sensitive company data. Database records, system files and data stored in the cloud should all be encrypted.
Security Affairs
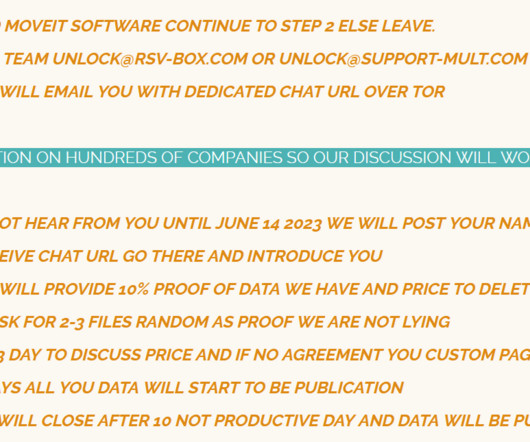
JUNE 16, 2023
WE ALSO WANT TO REMIND ALL COMPANY THAT IF YOU PUT DATA ON INTERNET WHERE DATA IS NOT PROTECT DO NOT BLAME US FOR PENETRATION TESTING SERVICE. ALL MEDIA SPEAKING ABOUT THIS ARE DO WHAT ALWAYS THEY DO. PROVIDE LITTLE TRUTH IN A BIG LIE. WE ARE ONLY FINANCIAL MOTIVATED AND DO NOT CARE ANYTHING ABOUT POLITICS.

Security Affairs
MARCH 17, 2021
According to the experts, the first infections were observed in late 2019, victims reported their files were encrypted by a strain of malware. locked to the filename of the encrypted files. The attackers implement a double extortion model using the PYSA ransomware to exfiltrate data from victims prior to encrypting their files.
Security Affairs
MARCH 18, 2023
” By protecting the code with encryption, the latest LockBit version can avoid the detection of signature-based anti-malware solutions. The RaaS’s affiliates use the following tools to exfiltrate data before encrypting it: Stealbit, a custom exfiltration tool used previously with LockBit 2.0; ” continues the report.

Security Affairs
JUNE 16, 2023
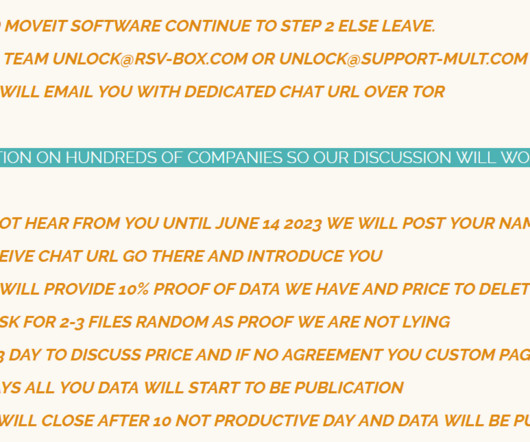
The group published the following message on its leak site to clarify the theft of data from government agencies reported by some media: “ WE GOT A LOT OF EMAILS ABOUT GOVERNMENT DATA, WE DON’T HAVE ANY GOVERNMENT DATA AND ANYTHING DIRECTLY RESIDING ON EXPOSED AND BAD PROTECTED NOT ENCRYPTED FILE TRANSFER WE STILL DO THE POLITE THING AND DELETE ALL.
Security Affairs
JUNE 18, 2023
WE ALSO WANT TO REMIND ALL COMPANY THAT IF YOU PUT DATA ON INTERNET WHERE DATA IS NOT PROTECT DO NOT BLAME US FOR PENETRATION TESTING SERVICE. ALL MEDIA SPEAKING ABOUT THIS ARE DO WHAT ALWAYS THEY DO. PROVIDE LITTLE TRUTH IN A BIG LIE. WE ARE ONLY FINANCIAL MOTIVATED AND DO NOT CARE ANYTHING ABOUT POLITICS.

SecureList
NOVEMBER 22, 2022
These are attractive aspects that cybercrime groups will be unable to resist. And not only cybercrime groups, but also state-sponsored groups who have already started targeting this industry. In the past, many actors would join forces to attack and encrypt as many organizations around the world as possible.

Malwarebytes
APRIL 20, 2021
In 2018 three high-ranking members of a sophisticated international cybercrime group operating out of Eastern Europe were arrested and taken into custody by US authorities. Hladyr also controlled the organization’s encrypted channels of communication.

SecureWorld News
AUGUST 8, 2022
Also known as Gozi, Ursnif has evolved over the years to include a persistence mechanism, methods to avoid sandboxes and virtual machines, and search capability for disk encryption software to attempt key extraction for unencrypting files. Remcos Remcos is marketed as a legitimate software tool for remote management and penetration testing.

Security Affairs
OCTOBER 14, 2019
Cybercrime gang behind the Emotet malware is targeting organization with external SOC with emails claiming to deliver a SOC “weekly report.”. AV and plenty static traffic signatures confirm we are facing a new encrypted version of Emotet trojan. Introduction. Conclusion.

SecureList
DECEMBER 14, 2021
The result of the command is encrypted (as previously described) and returned to the operator. The same username also exists as an account on RAID Forums, demonstrating an interest in Core Impact, a popular penetration testing software suite: s3crt RAID Forums account.

SecureList
MAY 8, 2024
It utilizes customizable attack vectors, including deceptive tactics like a fake Windows Update screen displayed to mask the file encryption process, and employs security measures for testing purposes, such as checking for “Vaccine.txt” before executing.

Cytelligence
JANUARY 27, 2020
Cybercriminals or threat actors release a kind of malware which enters a computer system or network through fraudulent means and locks down files from access by encrypting them until a demanded ransom is paid to hackers in return for a decryption key. Ransomware is a devastating attack on an organization’s or individual’s digital assets.

Malwarebytes
MAY 31, 2022
Cyberint’s Shmuel Gihon indicated that RansomHouse is “practically forcing ‘penetration testing service’ on organizations that never used their services or rewarded bug bounties.” They also reportedly do not encrypt files they stole from organizations. Links with ransomware groups.

Security Affairs
APRIL 1, 2019
About the Author: Odisseus – Independent Security Researcher involved in Italy and worldwide in topics related to hacking, penetration testing and development. Further details of this family of ELF malware we posted regularly in here:–>[link]”. But what are the machine info and how are they collected?

Krebs on Security
OCTOBER 8, 2020
There’s an old adage in information security: “Every company gets penetration tested, whether or not they pay someone for the pleasure.” ” Many organizations that do hire professionals to test their network security posture unfortunately tend to focus on fixing vulnerabilities hackers could use to break in.

eSecurity Planet
DECEMBER 3, 2021
Brian Krebs is an independent investigative reporter known for his coverage of technology, malware , data breaches , and cybercrime developments. Through tenures at Citrix, HP, and Bugcrowd, Jason Haddix offers his expertise in the areas of penetration testing , web application testing, static analysis, and more.

SecureWorld News
SEPTEMBER 15, 2023
Here are just some of the types of cybercrime that could jeopardize the safety of digital media assets: External attacks : Cybercriminals may attempt to breach company networks or systems to steal sensitive assets through phishing emails, brute force, or DDoS attacks.
Security Affairs
NOVEMBER 25, 2019
Many of them (almost 400k) hid a PE file compressed and/or encrypted into themselves. Many samples look like they open-up a local communication port which often hides a local proxy for encrypt communication between the malware and its command and control. TOP Matched Rules. Most APT Signature Metches.

SC Magazine
MARCH 10, 2021
“When an attacker gains access to surveillance cameras, the amount of knowledge which stands to be gained could be vast and poses a very real physical security threat,” said James Smith, principal security consultant and head of penetration testing at Bridewell Consulting.

eSecurity Planet
AUGUST 13, 2021
As cybercrime flourishes and evolves, organizations need a fleet of tools to defend and investigate incidents. Be it advanced locks, encryption barriers, or deleted and unknown content, the UFED (Universal Forensic Extraction Device) can extract physical and logical data.

Security Affairs
AUGUST 31, 2018
Now I was able to see encrypted URLs coming from infected hosts. Among many URLs the analyst was able to figure out a “test” connection from the Attacker and focus to decrypt such a connection. I do have experience on security testing since I have been performing penetration testing on several US electronic voting systems.
Krebs on Security
MAY 11, 2021
Here’s a closer look at the DarkSide cybercrime gang, as seen through their negotiations with a recent U.S. From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.” The advertisement continued: “Network penetration testing.

Herjavec Group
AUGUST 26, 2021
We can learn a lot from the cybercrime of the past…the history of cybercrime is a glimpse into what we can expect in the future. In the past 18 months, we’ve experienced the beginning of an era that has seen cybersecurity and cybercrime at the center of it all. Dateline Cybercrime . Robert Herjavec.

ForAllSecure
JUNE 21, 2022
You want to make sure that you're there no matter what they do with their laptop or computer and cyber criminals started adapting the same they said, You know what I want to collect your credit card whenever I want to gather your data whenever so you're exactly right of this technique transformed and now it's part of everyday cybercrime.

Krebs on Security
MARCH 4, 2022
.” Conti managers were hyper aware that their employees handled incredibly sensitive and invaluable data stolen from companies, information that would sell like hotcakes on the underground cybercrime forums. We want to inform that your company local network have been hacked and encrypted. “We are Conti Group.
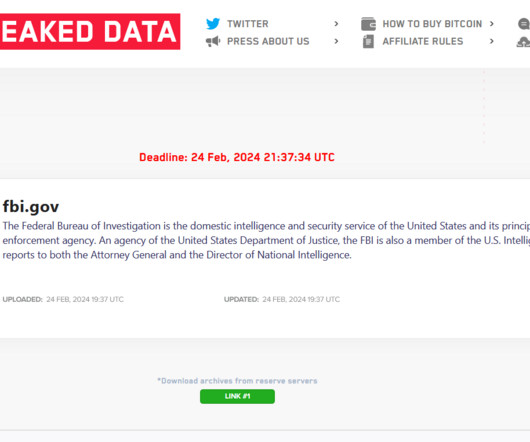
Security Affairs
FEBRUARY 25, 2024
The NCA will reach out to victims based in the UK in the coming days and weeks, providing support to help them recover encrypted data. version installed, which was successfully penetration tested most likely by this CVE [link] , as a result of which access was gained to the two main servers where this version of PHP was installed.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content