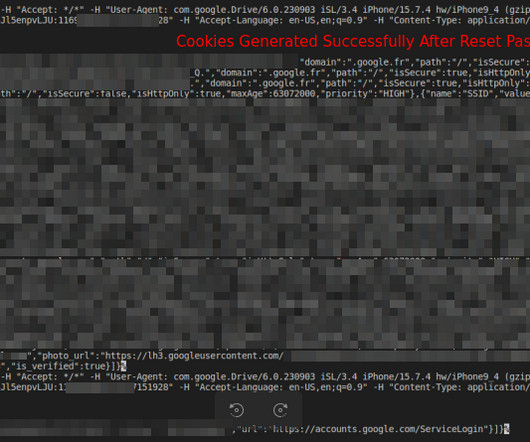
Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies
Security Affairs
JANUARY 1, 2024
An attacker can use the exploit to access Google services, even after a user’s password reset. The encrypted tokens are decrypted using an encryption key stored in Chrome’s Local State within the UserData directory, similar to the encryption used for storing passwords.” iPhone/15.7.4























Let's personalize your content