Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies
Security Affairs
JANUARY 1, 2024
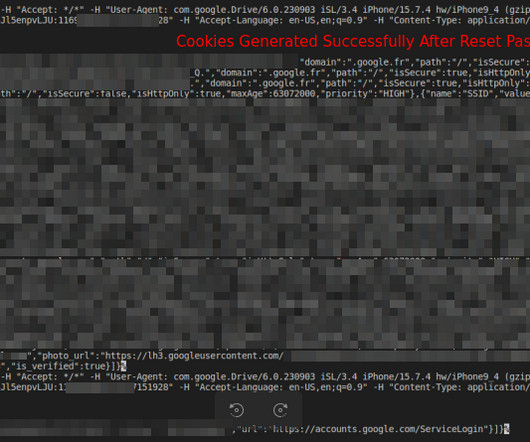
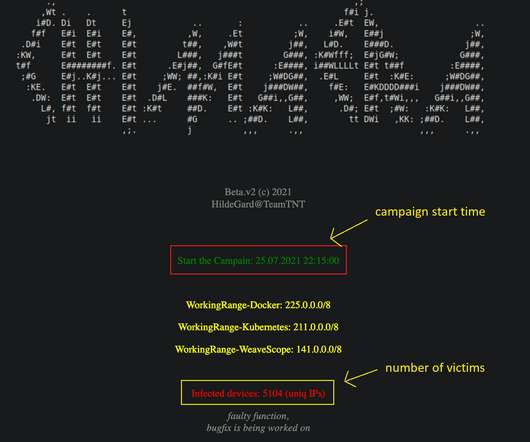
Subsequently, other malware integrated the exploit, including Rhadamanthys, Risepro, Meduza , Stealc Stealer and recently the White Snake. The researchers discovered that the malware targets Chrome’s token_service table of WebData to extract tokens and account IDs of chrome profiles logged in. ” continues the report.







































Let's personalize your content