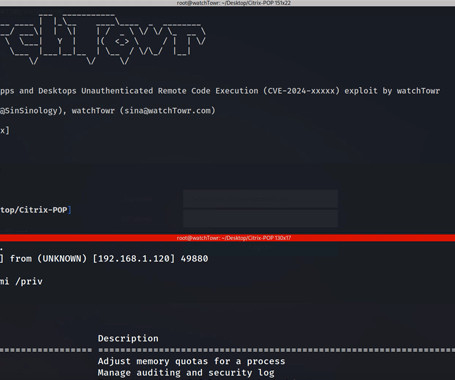
CVE-2025-2774: Webmin Vulnerability Allows Root-Level Privilege Escalation
Penetration Testing
MAY 3, 2025
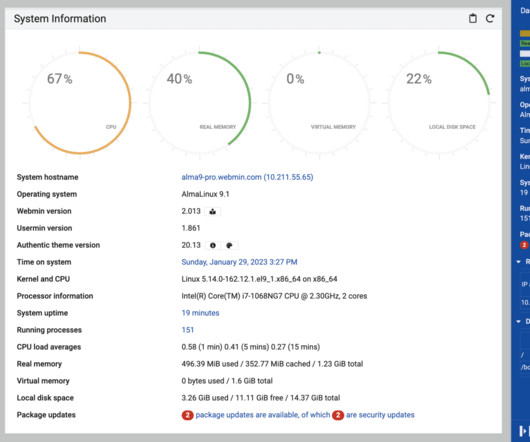
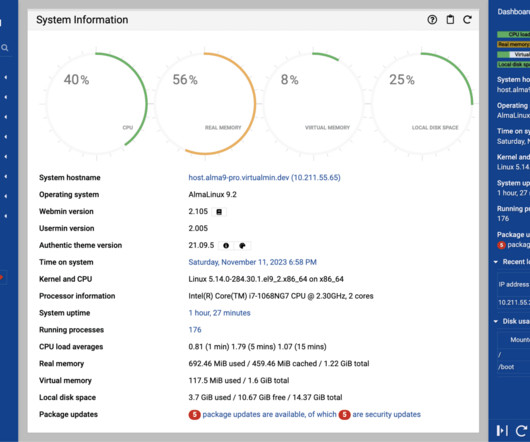
Webmin, a popular web-based system administration tool used to manage Unix-like servers and various services with approximately 1,000,000 The post CVE-2025-2774: Webmin Vulnerability Allows Root-Level Privilege Escalation appeared first on Daily CyberSecurity.









































Let's personalize your content